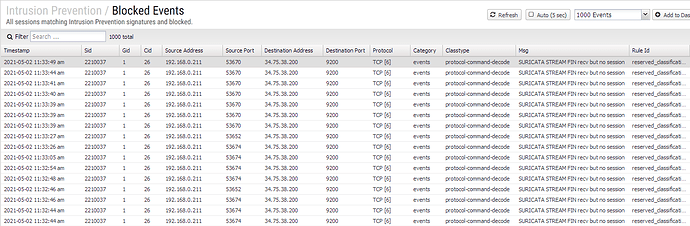
Hi Harry,
the connections to port 9200 of unidentified servers on the net doesn’t seem to have anything to do with Ropieee in and of itself, other than ofcourse that Ropieee is a Roon Bridge. It seems to be the Roon software talking with an array of servers out there.
I come to that conclusion after I downloaded the latest Ropieee bin and rewrote the SD card of the Pi, re-configured Ropieee, watching the entire time with the packet tracer.
Here we see the RoonServer and Ropieee talking with whatever is out there at exactly the same time.
wap-wsp = port 9200
192.168.0.10 = RoonServer
192.168.0.211 = Ropieee
13:51:25.158741 IP 192.168.0.10.35676 > 34.73.66.119.wap-wsp: Flags [P.], seq 1013187616:1013187617, ack 979881604, win 229, options [nop,nop,TS val 1679650987 ecr 16
3530060], length 1
13:51:25.158746 IP 192.168.0.10.35676 > 34.73.66.119.wap-wsp: Flags [P.], seq 0:1, ack 1, win 229, options [nop,nop,TS val 1679650987 ecr 163530060], length 1
13:51:25.240857 IP 192.168.0.211.57874 > 34.73.66.119.wap-wsp: Flags [P.], seq 2054820151:2054820152, ack 1876550703, win 256, length 1
13:51:25.240865 IP 192.168.0.211.57874 > 34.73.66.119.wap-wsp: Flags [P.], seq 0:1, ack 1, win 256, length 1
Here’s more detail of the connections comming from Ropieee:
14:01:25.241912 IP 192.168.0.211.57874 > 34.73.66.119.wap-wsp: Flags [P.], seq 2054820153:2054820154, ack 1876550703, win 256, length 1
14:01:25.241917 IP 192.168.0.211.57874 > 34.73.66.119.wap-wsp: Flags [P.], seq 0:1, ack 1, win 256, length 1
14:02:07.326762 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [S], seq 3987561449, win 32767, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
14:02:07.326767 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [S], seq 3987561449, win 32767, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
14:02:07.439046 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [.], ack 2870230337, win 256, length 0
14:02:07.439051 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [.], ack 1, win 256, length 0
14:02:07.439624 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [P.], seq 0:10, ack 1, win 256, length 10
14:02:07.439628 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [P.], seq 0:10, ack 1, win 256, length 10
14:02:07.440063 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [P.], seq 10:57, ack 1, win 256, length 47
14:02:07.440066 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [P.], seq 10:57, ack 1, win 256, length 47
14:02:50.794941 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [F.], seq 57, ack 1, win 256, length 0
14:02:50.794950 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [F.], seq 57, ack 1, win 256, length 0
14:02:50.795188 IP 192.168.0.211.57874 > 34.73.66.119.wap-wsp: Flags [F.], seq 1, ack 1, win 256, length 0
14:02:50.795202 IP 192.168.0.211.57874 > 34.73.66.119.wap-wsp: Flags [F.], seq 1, ack 1, win 256, length 0
14:02:50.906220 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [.], ack 2, win 256, length 0
14:02:50.906226 IP 192.168.0.211.57888 > 34.73.66.119.wap-wsp: Flags [.], ack 2, win 256, length 0
14:03:44.694558 IP 192.168.0.211.33706 > 34.73.66.119.wap-wsp: Flags [S], seq 2325666816, win 32767, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
14:03:44.694565 IP 192.168.0.211.33706 > 34.73.66.119.wap-wsp: Flags [S], seq 2325666816, win 32767, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
14:03:44.805816 IP 192.168.0.211.33706 > 34.73.66.119.wap-wsp: Flags [.], ack 753614251, win 256, length 0
14:03:44.805820 IP 192.168.0.211.33706 > 34.73.66.119.wap-wsp: Flags [.], ack 1, win 256, length 0
14:03:44.807938 IP 192.168.0.211.33706 > 34.73.66.119.wap-wsp: Flags [P.], seq 0:10, ack 1, win 256, length 10
14:03:44.807941 IP 192.168.0.211.33706 > 34.73.66.119.wap-wsp: Flags [P.], seq 0:10, ack 1, win 256, length 10
14:03:44.808551 IP 192.168.0.211.33706 > 34.73.66.119.wap-wsp: Flags [P.], seq 10:57, ack 1, win 256, length 47
14:03:44.808555 IP 192.168.0.211.33706 > 34.73.66.119.wap-wsp: Flags [P.], seq 10:57, ack 1, win 256, length 47
14:08:44.811010 IP 192.168.0.211.33706 > 34.73.66.119.wap-wsp: Flags [P.], seq 57:58, ack 1, win 256, length 1
14:08:44.811017 IP 192.168.0.211.33706 > 34.73.66.119.wap-wsp: Flags [P.], seq 57:58, ack 1, win 256, length 1
Dear @support what does RoonServer and RoonBridge do talking to port 9200 of various IPs on the internet, such as
35.237.106.222
35.227.6.128
34.75.196.16
104.196.205.85
35.243.240.56
35.196.73.153
34.73.66.119
?
And… is it important? I assume it’s fine that my firewall thinks this an intrusion attempt and (atleast partially) blocks the sessions.
Sincerely
Chris