I of course agree with you that as long as it’s handled well, it’s fine. I’m not an infosec guy, but my understanding is that the answer to “how dangerous is it” is “how much do you trust the RoonLab guys not to screw up ?”. I don’t at all, not because I don’t think they’re highly competent, but because they’re human, and screwing up’s what even the most competent humans sometimes do.
Then there’s how risk-averse you are: I’d consider going out to a nightclub and having unprotected sex as dangerous because AIDS, even though, especially as a heterosexual male, it statistically isn’t that risky (0.08% per act or something). Despite those low odds, I’m the kind that thinks unprotected sex with strangers is irresponsible, stupid, and super-dangerous.
Likewise, given the well-documented security screwups even by people whose job it is to not screw up (think LastPass and HackingTeam), and the potential risks involved, not having a second layer of protection truly seems irresponsible to me.
It’s also impossible to answer your “how dangerous is it really” question without a full audit, and it’d likely be granular, with differences between OS’s, networking setups, and what kind of stuff each user has on their home computer. But keeping in mind the failures of others, are you willing to gamble a takeover of your identity, or bank account, on a company’s diligence at cloud security ? Since it’s realistically impossible to avoid it, I’d rather have the odds be as good as possible, and I’d rather be on the more alarmist than on the more laidback side by considering not having added layers to mitigate very human screwups is “super, super dangerous”, but to each their own.
Also, I wouldn’t be surprised if RoonLabs wan’t the lowest-hanging fruit in your (or my) house, let alone in the Roon ecosystem. How much do you trust your endpoint vendor’s security ? 
 I bet Roon core doesn’t need root permissions. It doesn’t even ask for admin rights on Windows when installing.
I bet Roon core doesn’t need root permissions. It doesn’t even ask for admin rights on Windows when installing.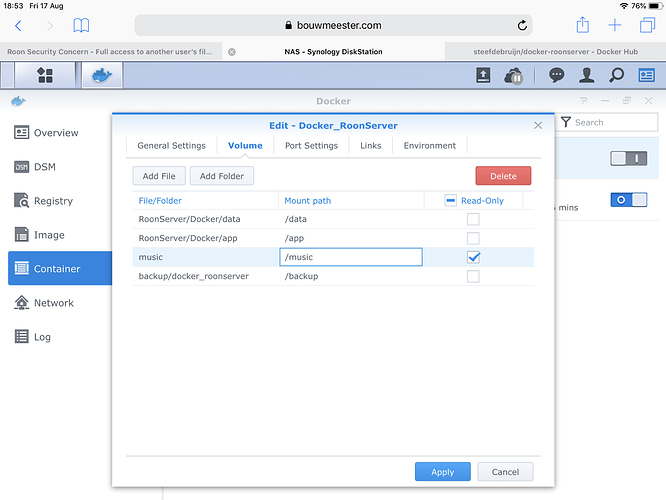




 All the other endpoint devices aren’t allowed to connect to the internet. The beauty of RAAT is that it’s designed to not need constant updates. And if one doesn’t go for music streaming services no internet is needed for those endpoint devices.
All the other endpoint devices aren’t allowed to connect to the internet. The beauty of RAAT is that it’s designed to not need constant updates. And if one doesn’t go for music streaming services no internet is needed for those endpoint devices.