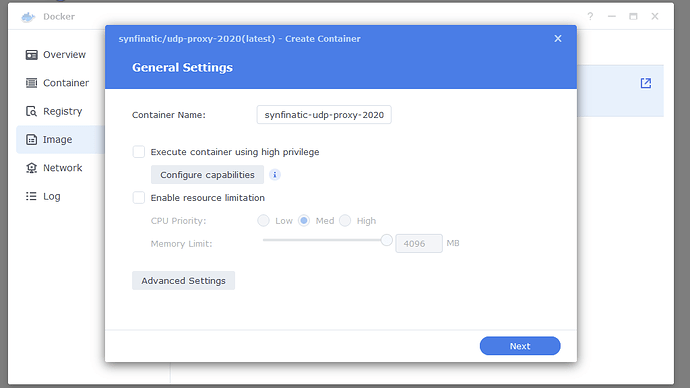
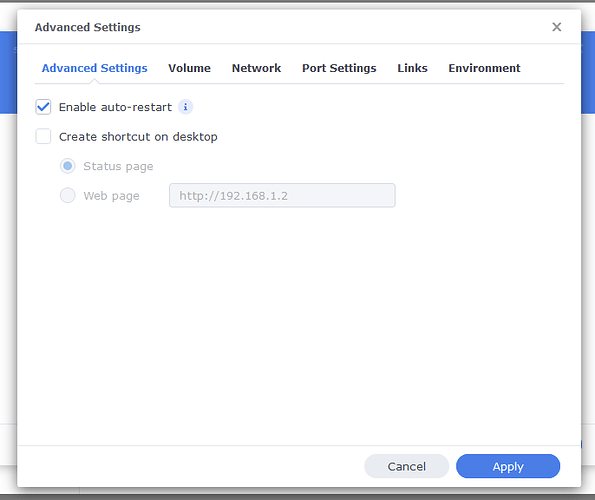
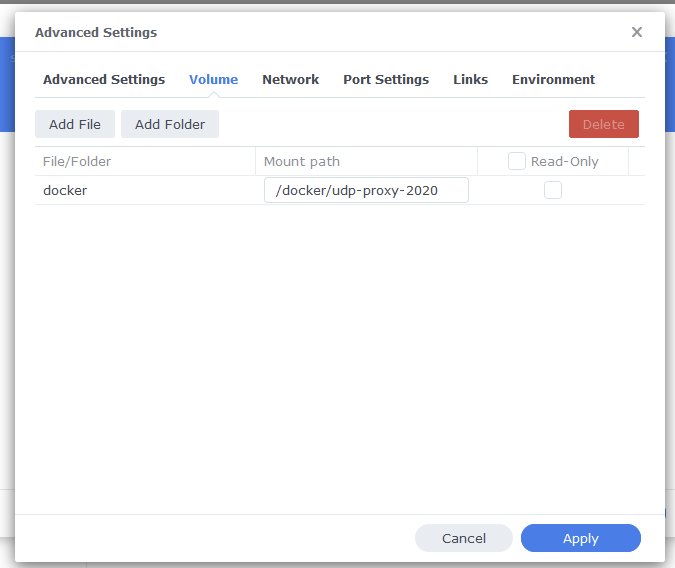
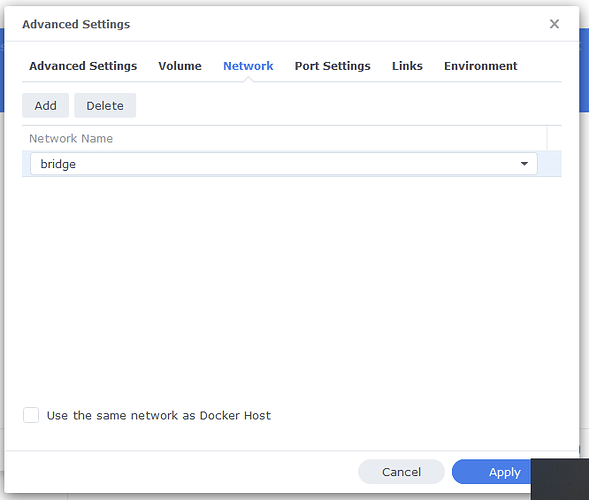
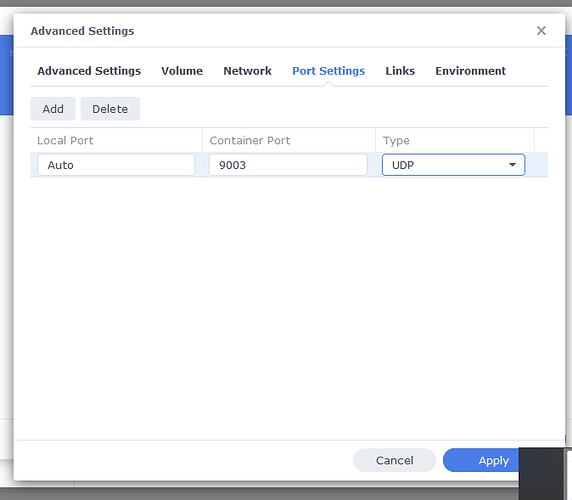
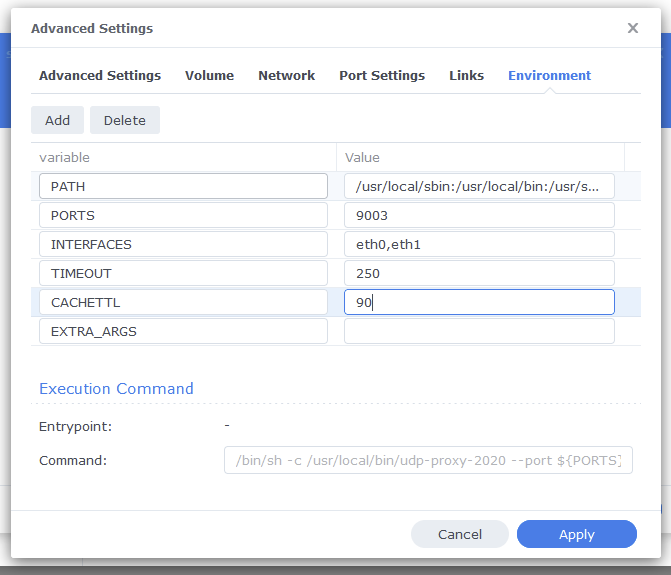
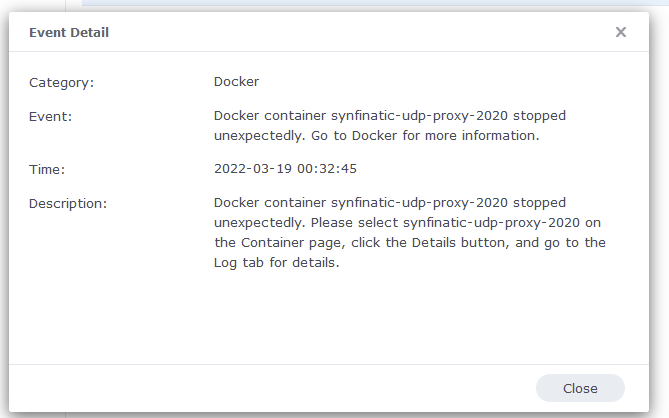
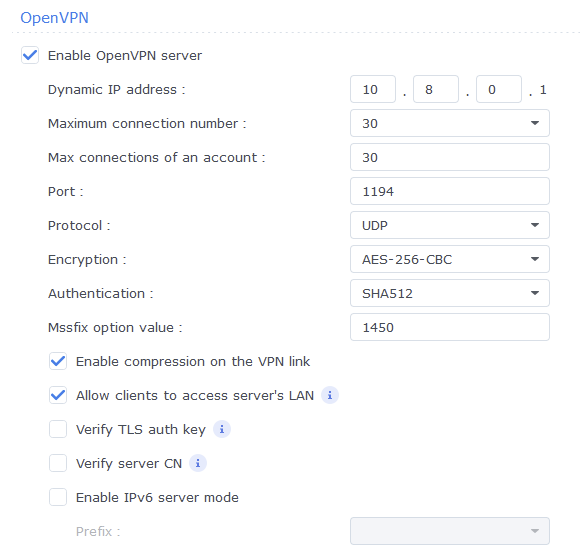
I tried first to install an OpenVPN server on my Mac but the info I’ve found was very scarce and then stumbled on a very complete tutorial on how to run a Wireguard server on a Mac and now I have a Wireguard server running and working :))
I’m strugling now on the udp-proxy-2020 part.
I installed the udp-proxy-2020-0.0.8-darwin-amd64 binary which is the one I should be running if I got it right (I’m using an Intel iMac on OS X 10.13.6) but when I run it I get the following:
iMac27-home:udp-proxy-2020 xavier$ ./udp-proxy-2020-0.0.8-darwin-amd64
fatal error: unexpected signal during runtime execution
[signal SIGSEGV: segmentation violation code=0x1 addr=0xb01dfacedebac1e pc=0x7fff5edd130a]
runtime stack:
runtime: unexpected return pc for runtime.sigpanic called from 0x7fff5edd130a
stack: frame={sp:0x7ffeefbff948, fp:0x7ffeefbff998} stack=[0x7ffeefb809e8,0x7ffeefbffa50)
0x00007ffeefbff848: 0x01007ffeefbff868 0x0000000000000004
0x00007ffeefbff858: 0x000000000000001f 0x00007fff5edd130a
0x00007ffeefbff868: 0x0b01dfacedebac1e 0x0000000000000001
0x00007ffeefbff878: 0x00000000040346b1 <runtime.throw+0x0000000000000071> 0x00007ffeefbff918
0x00007ffeefbff888: 0x00000000041c89cf 0x00007ffeefbff8d0
0x00007ffeefbff898: 0x0000000004034968 <runtime.fatalthrow.func1+0x0000000000000048> 0x00000000043449e0
0x00007ffeefbff8a8: 0x0000000000000001 0x0000000000000001
0x00007ffeefbff8b8: 0x00007ffeefbff918 0x00000000040346b1 <runtime.throw+0x0000000000000071>
0x00007ffeefbff8c8: 0x00000000043449e0 0x00007ffeefbff908
0x00007ffeefbff8d8: 0x00000000040348f0 <runtime.fatalthrow+0x0000000000000050> 0x00007ffeefbff8e8
0x00007ffeefbff8e8: 0x0000000004034920 <runtime.fatalthrow.func1+0x0000000000000000> 0x00000000043449e0
0x00007ffeefbff8f8: 0x00000000040346b1 <runtime.throw+0x0000000000000071> 0x00007ffeefbff918
0x00007ffeefbff908: 0x00007ffeefbff938 0x00000000040346b1 <runtime.throw+0x0000000000000071>
0x00007ffeefbff918: 0x00007ffeefbff920 0x00000000040346e0 <runtime.throw.func1+0x0000000000000000>
0x00007ffeefbff928: 0x00000000041cc41f 0x000000000000002a
0x00007ffeefbff938: 0x00007ffeefbff988 0x0000000004049cb6 <runtime.sigpanic+0x0000000000000396>
0x00007ffeefbff948: <0x00000000041cc41f 0x00000000043449e0
0x00007ffeefbff958: 0x00007ffeefbff9c8 0x0000000004027ba6 <runtime.(*mheap).allocSpan+0x0000000000000546>
0x00007ffeefbff968: 0x000000c0001d0000 0x0000000000002000
0x00007ffeefbff978: 0x0000000000000008 0x00000000040645c0 <runtime.walltime_trampoline+0x0000000000000000>
0x00007ffeefbff988: 0x00007ffeefbff9d0 !0x00007fff5edd130a
0x00007ffeefbff998: >0x00007ffeefbff9d0 0x0000000004328000
0x00007ffeefbff9a8: 0x0000000000000163 0x0000000004120e05 <golang.org/x/sys/unix.libc_ioctl_trampoline+0x0000000000000005>
0x00007ffeefbff9b8: 0x0000000004064bff <runtime.syscall+0x000000000000001f> 0x000000c0001b1078
0x00007ffeefbff9c8: 0x000000000406456c <runtime.nanotime_trampoline+0x000000000000000c> 0x000000c0001b1048
0x00007ffeefbff9d8: 0x0000000004062a90 <runtime.asmcgocall+0x0000000000000070> 0x0000000000000001
0x00007ffeefbff9e8: 0x0000000004001400 0x1400000000001018
0x00007ffeefbff9f8: 0x0000000000000010 0x00000000048a3ad8
0x00007ffeefbffa08: 0x0000000000000fe0 0x000000c0000001a0
0x00007ffeefbffa18: 0x0000000004060ba9 <runtime.systemstack+0x0000000000000049> 0x0000000000000004
0x00007ffeefbffa28: 0x00000000041f6f68 0x00000000043449e0
0x00007ffeefbffa38: 0x00007ffeefbffa80 0x0000000004060aa5 <runtime.mstart+0x0000000000000005>
0x00007ffeefbffa48: 0x0000000004060a5d <runtime.rt0_go+0x000000000000013d>
runtime.throw({0x41cc41f, 0x43449e0})
/usr/local/Cellar/go/1.17.2/libexec/src/runtime/panic.go:1198 +0x71
runtime: unexpected return pc for runtime.sigpanic called from 0x7fff5edd130a
stack: frame={sp:0x7ffeefbff948, fp:0x7ffeefbff998} stack=[0x7ffeefb809e8,0x7ffeefbffa50)
0x00007ffeefbff848: 0x01007ffeefbff868 0x0000000000000004
0x00007ffeefbff858: 0x000000000000001f 0x00007fff5edd130a
0x00007ffeefbff868: 0x0b01dfacedebac1e 0x0000000000000001
0x00007ffeefbff878: 0x00000000040346b1 <runtime.throw+0x0000000000000071> 0x00007ffeefbff918
0x00007ffeefbff888: 0x00000000041c89cf 0x00007ffeefbff8d0
0x00007ffeefbff898: 0x0000000004034968 <runtime.fatalthrow.func1+0x0000000000000048> 0x00000000043449e0
0x00007ffeefbff8a8: 0x0000000000000001 0x0000000000000001
0x00007ffeefbff8b8: 0x00007ffeefbff918 0x00000000040346b1 <runtime.throw+0x0000000000000071>
0x00007ffeefbff8c8: 0x00000000043449e0 0x00007ffeefbff908
0x00007ffeefbff8d8: 0x00000000040348f0 <runtime.fatalthrow+0x0000000000000050> 0x00007ffeefbff8e8
0x00007ffeefbff8e8: 0x0000000004034920 <runtime.fatalthrow.func1+0x0000000000000000> 0x00000000043449e0
0x00007ffeefbff8f8: 0x00000000040346b1 <runtime.throw+0x0000000000000071> 0x00007ffeefbff918
0x00007ffeefbff908: 0x00007ffeefbff938 0x00000000040346b1 <runtime.throw+0x0000000000000071>
0x00007ffeefbff918: 0x00007ffeefbff920 0x00000000040346e0 <runtime.throw.func1+0x0000000000000000>
0x00007ffeefbff928: 0x00000000041cc41f 0x000000000000002a
0x00007ffeefbff938: 0x00007ffeefbff988 0x0000000004049cb6 <runtime.sigpanic+0x0000000000000396>
0x00007ffeefbff948: <0x00000000041cc41f 0x00000000043449e0
0x00007ffeefbff958: 0x00007ffeefbff9c8 0x0000000004027ba6 <runtime.(*mheap).allocSpan+0x0000000000000546>
0x00007ffeefbff968: 0x000000c0001d0000 0x0000000000002000
0x00007ffeefbff978: 0x0000000000000008 0x00000000040645c0 <runtime.walltime_trampoline+0x0000000000000000>
0x00007ffeefbff988: 0x00007ffeefbff9d0 !0x00007fff5edd130a
0x00007ffeefbff998: >0x00007ffeefbff9d0 0x0000000004328000
0x00007ffeefbff9a8: 0x0000000000000163 0x0000000004120e05 <golang.org/x/sys/unix.libc_ioctl_trampoline+0x0000000000000005>
0x00007ffeefbff9b8: 0x0000000004064bff <runtime.syscall+0x000000000000001f> 0x000000c0001b1078
0x00007ffeefbff9c8: 0x000000000406456c <runtime.nanotime_trampoline+0x000000000000000c> 0x000000c0001b1048
0x00007ffeefbff9d8: 0x0000000004062a90 <runtime.asmcgocall+0x0000000000000070> 0x0000000000000001
0x00007ffeefbff9e8: 0x0000000004001400 0x1400000000001018
0x00007ffeefbff9f8: 0x0000000000000010 0x00000000048a3ad8
0x00007ffeefbffa08: 0x0000000000000fe0 0x000000c0000001a0
0x00007ffeefbffa18: 0x0000000004060ba9 <runtime.systemstack+0x0000000000000049> 0x0000000000000004
0x00007ffeefbffa28: 0x00000000041f6f68 0x00000000043449e0
0x00007ffeefbffa38: 0x00007ffeefbffa80 0x0000000004060aa5 <runtime.mstart+0x0000000000000005>
0x00007ffeefbffa48: 0x0000000004060a5d <runtime.rt0_go+0x000000000000013d>
runtime.sigpanic()
/usr/local/Cellar/go/1.17.2/libexec/src/runtime/signal_unix.go:719 +0x396
goroutine 1 [syscall]:
syscall.syscall(0x4120e00, 0x2, 0x40487413, 0xc0001b1108)
/usr/local/Cellar/go/1.17.2/libexec/src/runtime/sys_darwin.go:22 +0x3b fp=0xc0001b1078 sp=0xc0001b1058 pc=0x405f87b
syscall.syscall(0xc, 0x1a, 0x41f9660, 0x41cfc08)
<autogenerated>:1 +0x26 fp=0xc0001b10c0 sp=0xc0001b1078 pc=0x4065326
golang.org/x/sys/unix.ioctl(0x15, 0x41f9660, 0x41cfc08)
/Users/aturner/go/pkg/mod/golang.org/x/sys@v0.0.0-20200930185726-fdedc70b468f/unix/zsyscall_darwin_amd64.go:731 +0x39 fp=0xc0001b10f0 sp=0xc0001b10c0 pc=0x4120a99
golang.org/x/sys/unix.IoctlGetTermios(...)
/Users/aturner/go/pkg/mod/golang.org/x/sys@v0.0.0-20200930185726-fdedc70b468f/unix/ioctl.go:72
github.com/sirupsen/logrus.isTerminal(0x4)
/Users/aturner/go/pkg/mod/github.com/sirupsen/logrus@v1.7.0/terminal_check_bsd.go:11 +0x50 fp=0xc0001b1160 sp=0xc0001b10f0 pc=0x41245b0
github.com/sirupsen/logrus.checkIfTerminal({0x41f9480, 0xc000010020})
/Users/aturner/go/pkg/mod/github.com/sirupsen/logrus@v1.7.0/terminal_check_notappengine.go:13 +0x75 fp=0xc0001b1178 sp=0xc0001b1160 pc=0x4124655
github.com/sirupsen/logrus.(*TextFormatter).init(0xc00005e240, 0x4b22328)
/Users/aturner/go/pkg/mod/github.com/sirupsen/logrus@v1.7.0/text_formatter.go:103 +0x34 fp=0xc0001b11f8 sp=0xc0001b1178 pc=0x4124734
github.com/sirupsen/logrus.(*TextFormatter).Format.func1()
/Users/aturner/go/pkg/mod/github.com/sirupsen/logrus@v1.7.0/text_formatter.go:193 +0x25 fp=0xc0001b1218 sp=0xc0001b11f8 pc=0x4125de5
sync.(*Once).doSlow(0x41fc170, 0xc00000e2a0)
/usr/local/Cellar/go/1.17.2/libexec/src/sync/once.go:68 +0xd2 fp=0xc0001b1280 sp=0xc0001b1218 pc=0x4070452
sync.(*Once).Do(...)
/usr/local/Cellar/go/1.17.2/libexec/src/sync/once.go:59
github.com/sirupsen/logrus.(*TextFormatter).Format(0xc00005e240, 0xc0001b88c0)
/Users/aturner/go/pkg/mod/github.com/sirupsen/logrus@v1.7.0/text_formatter.go:193 +0xebe fp=0xc0001b17f0 sp=0xc0001b1280 pc=0x412579e
github.com/sirupsen/logrus.(*Entry).write(0xc0001b88c0)
/Users/aturner/go/pkg/mod/github.com/sirupsen/logrus@v1.7.0/entry.go:271 +0xa5 fp=0xc0001b1868 sp=0xc0001b17f0 pc=0x4122ce5
github.com/sirupsen/logrus.Entry.log({0xc0001b8000, 0xc000068cc0, {0x0, 0x0, 0x0}, 0x0, 0x0, {0x0, 0x0}, 0x0, ...}, ...)
/Users/aturner/go/pkg/mod/github.com/sirupsen/logrus@v1.7.0/entry.go:247 +0x25a fp=0xc0001b18e0 sp=0xc0001b1868 pc=0x412297a
github.com/sirupsen/logrus.(*Entry).Log(0xc0001b8850, 0x1, {0xc0001b1d00, 0x4124186, 0x41488d8})
/Users/aturner/go/pkg/mod/github.com/sirupsen/logrus@v1.7.0/entry.go:283 +0xa8 fp=0xc0001b19e8 sp=0xc0001b18e0 pc=0x4122f08
github.com/sirupsen/logrus.(*Logger).Log(0xc0001b8000, 0x1, {0xc0001b1d00, 0x1, 0x1})
/Users/aturner/go/pkg/mod/github.com/sirupsen/logrus@v1.7.0/logger.go:198 +0x65 fp=0xc0001b1a28 sp=0xc0001b19e8 pc=0x4123e85
github.com/sirupsen/logrus.(*Logger).Fatal(0xc0001ca000, {0xc0001b1d00, 0xc000010020, 0x0})
/Users/aturner/go/pkg/mod/github.com/sirupsen/logrus@v1.7.0/logger.go:242 +0x31 fp=0xc0001b1a68 sp=0xc0001b1a28 pc=0x4123f51
github.com/sirupsen/logrus.Fatal(...)
/Users/aturner/go/pkg/mod/github.com/sirupsen/logrus@v1.7.0/exported.go:134
main.main()
/Users/aturner/go/src/github.com/synfinatic/udp-proxy-2020/cmd/main.go:84 +0x790 fp=0xc0001b1f80 sp=0xc0001b1a68 pc=0x4152ab0
runtime.main()
/usr/local/Cellar/go/1.17.2/libexec/src/runtime/proc.go:255 +0x227 fp=0xc0001b1fe0 sp=0xc0001b1f80 pc=0x4036d47
runtime.goexit()
/usr/local/Cellar/go/1.17.2/libexec/src/runtime/asm_amd64.s:1581 +0x1 fp=0xc0001b1fe8 sp=0xc0001b1fe0 pc=0x4062d81