the “Event Detail” says to look at the logs. did you look at them? Can you share them?
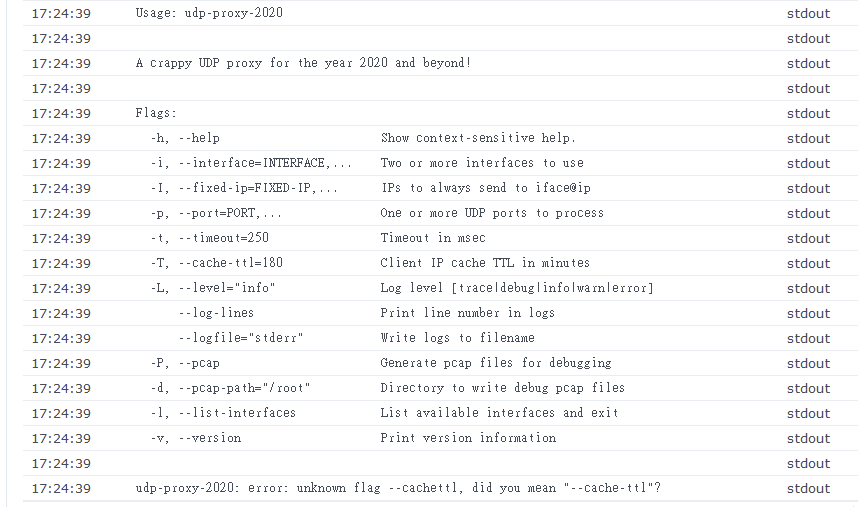
answer is in the logs 
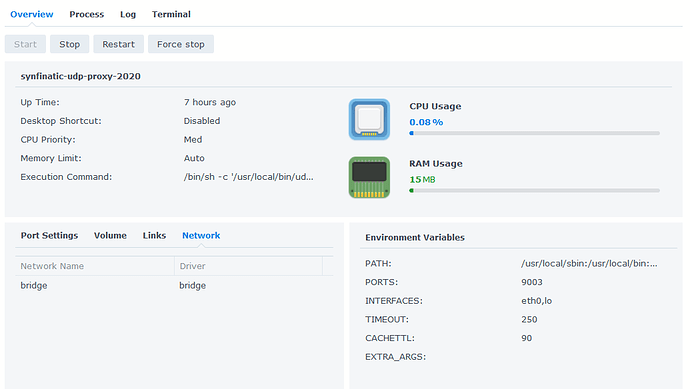
"unknown flag --cachettl, did you mean “–cache-ttl”?
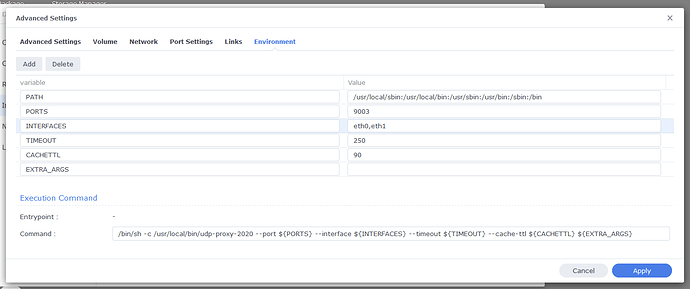
should I change the execution command?
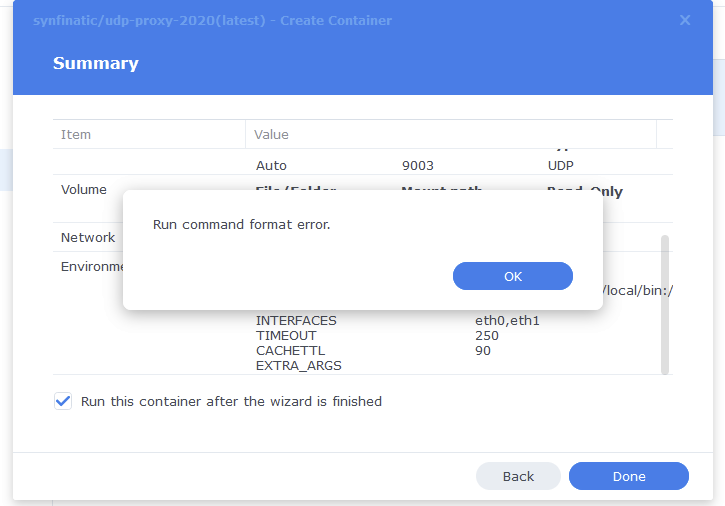
buts its fail : Run command format error…
I’m trying to telnet to the NAS using find command:
/volume2/docker/udp-proxy-2020
/volume2/@docker/btrfs/subvolumes/f7c9434d5d9b4abdf39832804f91ea6928e0d26dd7f2f1afcdb6daf74a6ae58e/usr/local/bin/udp-proxy-2020
/volume2/@docker/btrfs/subvolumes/2f2db5d9c35791d247b16980c2f37be40122a8f272e0325a5a1bbd050c6b91fd-init/usr/local/bin/udp-proxy-2020
/volume2/@docker/btrfs/subvolumes/2f2db5d9c35791d247b16980c2f37be40122a8f272e0325a5a1bbd050c6b91fd/usr/local/bin/udp-proxy-2020
/volume2/@docker/btrfs/subvolumes/2f2db5d9c35791d247b16980c2f37be40122a8f272e0325a5a1bbd050c6b91fd/docker/udp-proxy-2020
A few things:
- Download the latest Docker image: v0.0.10 and use that.
- You need to remove the bridge network and click the “use host network” option.
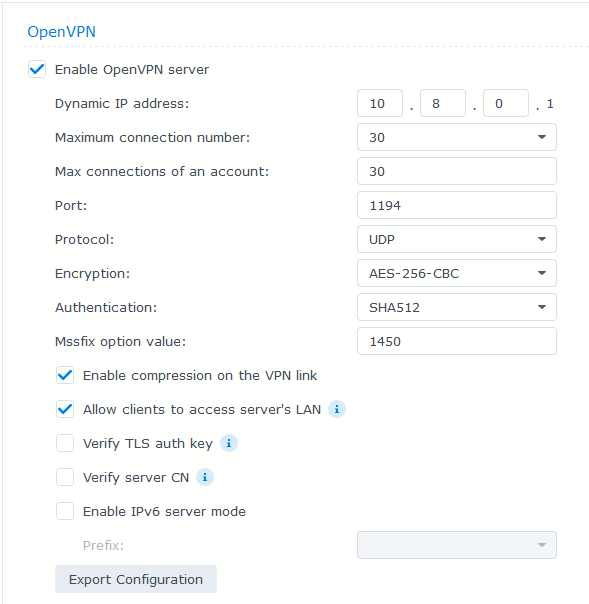
- Since you are using OpenVPN, you’ll need to list the tunnel interface in the list of INTERFACES
- Need to use “host networking” for the OpenVPN container too? Otherwise, I don’t think udp-proxy-2020 will be able to see the OpenVPN tunnel interface
Honestly, I don’t have the way or time to test every single combination and I don’t use the docker solution myself. It’s mostly there for the Ubiquiti Dream Machine people. What combination of bridge/host networking will likely have to be left up to you.
thanks, I will try to update it, & config later on.
planning to get a pair of edgerouter with pfsense, is it a good idea for site to site vpn?
used for using up-proxy-2020 with roon.
EdgeRouter is Ubiquiti? pfSense is very different.
Most people aren’t using udp-proxy-2020 for site-to-site, but it should work fine with IPSec (using virtual tunnel interface, not the more dynamic road warrior setup) or something like OpenVPN. Just realize you’ll need to run udp-proxy-2020 on both ends to forward the packets.
Download & installed Docker image v0.0.10 its working now! thanks
But can’t find the audio devices in the windows desktop roon client.
using terminal connected the synology with ifconfig shown as follow:
docker0 Link encap:Ethernet HWaddr ****************
inet addr:172.17.0.1 Bcast:172.17.255.255 Mask:255.255.0.0
inet6 addr: fe80::42:a3ff:fe98:67e1/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:3 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 B) TX bytes:258 (258.0 B)
docker540 Link encap:Ethernet HWaddr ***************
inet6 addr: fe80::542a:d0ff:fe1a:4e6c/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:6 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 B) TX bytes:516 (516.0 B)
eth0 Link encap:Ethernet HWaddr ***********
inet addr:192.168.1.2 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::211:32ff:fe3c:8105/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1829305 errors:0 dropped:0 overruns:0 frame:0
TX packets:890706 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2525034661 (2.3 GiB) TX bytes:244757290 (233.4 MiB)
eth1 Link encap:Ethernet HWaddr ***********
inet addr:169.254.250.189 Bcast:169.254.255.255 Mask:255.255.0.0
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
eth2 Link encap:Ethernet HWaddr *********
inet addr:169.254.177.197 Bcast:169.254.255.255 Mask:255.255.0.0
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
eth3 Link encap:Ethernet HWaddr ***********
inet addr:169.254.218.101 Bcast:169.254.255.255 Mask:255.255.0.0
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:898 errors:0 dropped:0 overruns:0 frame:0
TX packets:898 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:384796 (375.7 KiB) TX bytes:384796 (375.7 KiB)
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.8.0.1 P-t-P:10.8.0.2 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:1351373 errors:0 dropped:0 overruns:0 frame:0
TX packets:759097 errors:0 dropped:88 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:1812161458 (1.6 GiB) TX bytes:165305267 (157.6 MiB)
So I’m seeing the same thing on iOS with my iPhone, but oddly not with the MacOS client using both OpenVPN and Wireguard. The two clients are behaving a little differently, but honestly I don’t see anything wrong or broken with either. I’ve used Roon on my iPhone many times with success and now it also sees the output devices on the same network as the Roon Core, but does not see the phone itself as an output.
Anyways, I have an idea which may or may not pay off. Will update this thread when I have something to share.
So I have good news! I figured out what is going on!
TL;DR: you need to block UDP/9003 broadcast traffic on the VPN tunnel interface for your OpenVPN or Wireguard tunnel.
For example, if your OpenVPN (or Wireguard) VPN tunnel interface is 172.16.10.1/24 (netmask of 255.255.255.0) then you need to create a DROP rule on the VPN tunnel interface like this:
Source IP: Any
Destination IP: 172.16.10.255
Destination Port: UDP/9003
Action: Drop
What this does is prevent the firewall/router from generating ICMP Port Unavailable messages back to the iPhone/etc which is causing the problem.
Also, for those of you who don’t really understand the above instructions, have no fear! I have a plan on how to modify udp-proxy-2020 resolve this issue more gracefully. ![]()
Thanks Aaron!
You are a legend, I will try and give you a feedback.
For those of you who weren’t sure how to configure your firewall, I’ve released v0.0.11 of udp-proxy-2020 which implements a fix for the issue effecting iOS (and others?) over VPN:
Please note that if you are running the Roon Core on the same host as udp-proxy-2020 then you must now specify the --no-listen flag or things won’t work.
Hi @Aaron_Turner,
I am playing locally on the iPhone over OpenVPN using your udp-proxy-2020 on a daily basis without any issue. Thank you for this and your ongoing development. If possible let me know how I make a donation to support your work.
Thnx and regards,
Woody
Hi Woody,
I’m really glad to hear that udp-proxy-2020 works for you and makes your Roon experience better! I really wrote it for myself, because I enjoy Roon and wanted to listen on my phone and computer when I was away from home.
Honestly, I don’t need any money and your thanks is enough. If you (or anyone here) would still like to do something, feel free to make a donation to https://www.shfb.org which is my local food bank.
Regards,
Aaron
I have Roon running and when away from home, e.g. on iPhone using wireguard Roon starts and I can see all the local endpoints. The iPhone itself is no longer visible as an endpoint.
I use opnsense, I see that pfsense is supported. Anybody know how to get this to work on opnsense? or by using opnsense-plugin-UDP Broadcast Relay ?
Have you tried Aaron’s udp-proxy-2020?
yeah, that did not seem to work, I think, while wireguard runs on opnsense, this plugin needs to run there (?) but don’t know if the pfsense version is working on opnsense, or that the already available plugin UDP Broadcast Relay can do the job also…
Can you share more info about your setup? What VPN? How and where did you configure udp-proxy-2020? You’re running v0.0.11 right?
I don’t recall anyone on this thread using OpnSense so can’t really help with the included “UDP Broadcast Relay”. Honestly, I have no idea what that is or how it works.
Hi Aaron,
Quick feedback in v0.0.11. It works like a charm for me!
My configuration is:
- Roon core on an iMac
- wireguard on a Raspberry Pi
- udp-proxy-2020 v0.0.11 on the same Raspberry Pi
- I applied some changes to the route table on the iMac:
sudo networksetup -setadditionalroutes Ethernet 10.6.0.0 255.255.255.0 192.168.0.172
(10.6.0.x is the wireguard io range, 192.168.0.x is the home network, where both the Mac an the RPi are, 192.168.0.172 is the fixed IP of the RPi)
That’s it, so far, with the new v0.0.11 version, the phone is always seen as a audio zone when running Roon client on 4G and with VPN active. No more drop outs.
What can I say. Brilliant! Thanks a lot!
Edit:
It might be useful for someone, I start it with a systemd script:
root@rpi4:/opt/udp-proxy-2020/udp-proxy-2020-current# cat udp-proxy-2020.service
[Unit]
Description=udp-proxy-2020 - Use Roon over VPN
Requires=network.target
After=network.target
[Service]
ExecStart=/opt/udp-proxy-2020/udp-proxy-2020-current/udp-proxy-2020 --port 9003 --interface eth0,wg0 --cache-ttl 500
Restart=on-abort
[Install]
WantedBy=multi-user.target
I have a link to this file in /etc/systemd/system.
I can control udp-proxy-2020 with the usual systemctl commands (e.g. systemctl status udp-proxy-2020), it starts automatically at boot and so on.
I am using a kind of easy setup. ISP provider → opnsense box firewall and Wireguard → Synology NAS running ROON server.
I could run dup-proxy-2020 on the NAS but I think that would not help because of the WG0 / wireguard is running on opnsense. So I think the UDP should be running on the opnsense box?
The UDP Broadcast Relay plugin for opnsense is this one if I’m correct:
Since opnsense is started as a fork of pfsense, maybe it is easy to me made as an plugin there also?