I’ve realised that the wireguard installation is not preserved after a usg firmware upgrade. You can use vyatta-wireguard-installer to automatically install and reconfigure wireguard after firmware upgrades.
Hi,
I’m lost, I don’t have a Unifi USG, but UDM (UnifiOS), I still managed to install WireGuard, but I can’t install udp-proxy-2020.
Could someone explain me the procedure on UDM ?
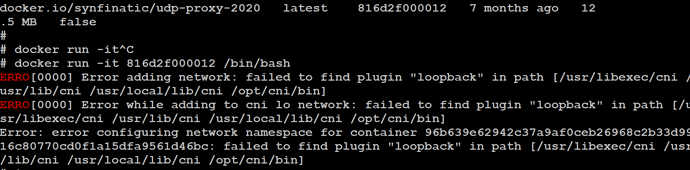
I have loaded the docker image, but when I try to run it, I get errors
I must be following the wrong procedure, but I have never used docker 
Thanks in advance
I don’t have a UDM or anything running UniFi OS so not really sure how much help I can be, but I googled “udm docker loopback” and found this:
I’d stick to using https://podman.io/ to manage containers on the UDM.
This guide is probably the best place to start.
You can see the actual podman commands that are run if you look at the end of the 40-udp-proxy-2020.sh script.
Although you may as well just run the wrapper script directly (or as an on_boot.d script on startup) as it will also check the configuration file for you.
I’d start by running the script manually and enable the debug flag in the udp-proxy-2020.conf config file, to ensure everything works before installing it as a startup script.
If you need to stop the container then podman ps and podman stop <containerid> will be what your looking for. podman logs --follow <containerid> will also be useful if you want to tail the debug logs.
Note: I think you’ll need to add/use wg0 (WireGuard) and br0 or similar (as the interface that sees your local network) rather than the eth0 interface used in Bart’s USG guide above as the UDM has a built in switch, whereas the USG eth0 port is connected to one. Once you have it running with logging turned on you should be able to see which interfaces have traffic on port 9003 and which don’t, you can also use tcpdump (limited to port 9003) to check which interfaces have traffic as well.
If you want to check which interfaces (ifconfig) on your local network is sending out UDP packets on you can use tcpdump -i br0 udp port 9003 and then restart a Roon control app and you should see a bunch of packets scroll past — if you don’t you likely have the wrong interface.
In my udp-proxy-2020.conf I use INTERFACES=br0,wg0 which works for me on my UDM Pro but if you have a more complex VLAN setup you may need to look for Roon’s UDP packets on a different interface.
FWIW I found I had most success with this version of Wireguard on the UDM Pro.
Hope that helps.
Dear J_a_m_i_e, dear Aaron
thank you very much for all these explanations, I will try to put all this in function, even if for the moment it is Chinese

I really must have a problem with my UDM
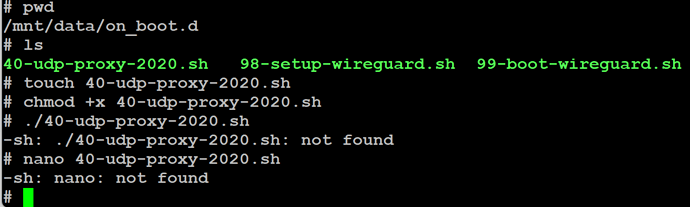
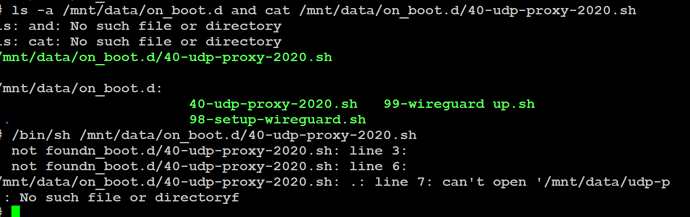
The script is there, but I can’t run it or open it!

so I’ll have to solve this problem first, but thanks again
j_a_m_i_e,
Sorry to bother you with my stupid question, but I already can’t install the upd-proxy-2020 container.
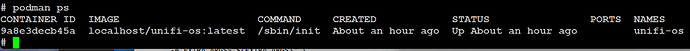
When i look at the ones I have, I only have unifi-os…
I can’t add upd-proxy-2020, can you explain me how to do this on my UDM?
And the second thing I don’t know how to do is to run a script manually,
when I try, I get this error:
there too there must be something I’m not doing right.
If you could explain me that too?
For the udp-proxy-2020.conf file, it’s all good, your explanation was perfect, it’s also br0 on the UDM
Many thanks in advance
David
I’m not sure why you can’t run the 40-udp-proxy-2020.sh script, it looks like your doing everything correctly.
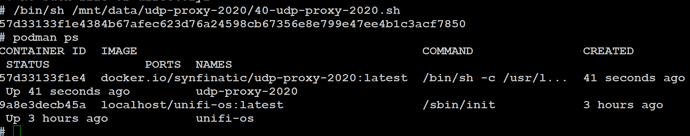
But once you figure that out, running 40-udp-proxy-2020.sh script should create and start the container for you. After which you should see it listed when running podman ps.
That should be the only thing you need to do assuming your Wireguard setup is configured and working correctly ie. you can already see the Roon Core via the VPN even without using udp-proxy-2020.
–
In terms of the nano error, the UDM doesn’t come with nano installed, you’ll have to use vi instead.
But as to the wider issue of why you can’t run the 40-udp-proxy-2020.sh script, I’m equally stumped. What do you see if you run ls -a /mnt/data/on_boot.d and cat /mnt/data/on_boot.d/40-udp-proxy-2020.sh
You could also try running it like this /bin/sh /mnt/data/on_boot.d/40-udp-proxy-2020.sh but that shouldn’t be necessary, what your doing in your screenshot above looks correct.
This Stack Overflow post suggest that this can be caused by CR LF issues. Although if you just copied the download file that shouldn’t be an issue.
Maybe try cut / pasting the script directly from GitHub (click the raw button) into a new file you have created yourself, possibly outside of the on_boot.d directory for now ie. somewhere like /mnt/data/udp-proxy-2020 to see if that makes any difference.
Thanks for all this information,
I quickly tested these 2 things, and indeed there are some strange things. but I just did a factory reset though…
But you had a good intuition, apart from on_boot.d, it worked
I should be able to make it work now
Thank you so much for your help
David
Glad that helped, sounds like you’re almost there.
I actually meant for you to run those two commands on separate lines ie.
ls -a /mnt/data/on_boot.d
cat /mnt/data/on_boot.d/40-udp-proxy-2020.sh
But now you have it working outside the on_boot.d directory, you could try just making a copy of it into the on_boot.d directory ie cp /mnt/data/udp-proxy-2020/40-udp-proxy-2020.sh /mnt/data/on_boot.d/40-udp-proxy-2020.sh and seeing if you can then see / run it correctly from there.
If it still doesn’t work I’d slowly retrace your installation, specifically the udm-utilities bit under requirements and check you didn’t miss a step.
It looks like a permissions issues - I assume you’re logged in as root - but I’d be careful about changing permissions other than giving the 40-udp-proxy-2020.sh file execute permissions. Certainly don’t go charging permissions on any UDM file or directory that you didn’t create yourself.
I don’t seem to remember having to do anything outside of those steps, other than updating the interface in the config file to br0,wg0 to get it working on my UDM Pro.
Even if you can’t work out how to get it to run on startup, for now you can just start it manually after a reboot.
If you have logging turned on in the UDP-proxy-2020 config file you may want to turn it off once you know everything is working, as it generates quite a lot of debug output.
You can stop the container with podman stop <containerid> (make sure you have the correct container id, as you don’t want to stop the main unifi-os container!) and then restart it again with the 40-udp-proxy-2020.sh script. You can find the container id in the first column when running podman ps



The more I test the less it works…
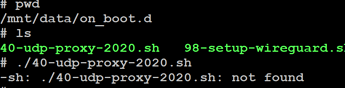
Now whether it’s in /mnt/data/on_boot.d/ or in /mnt/data/udp-proxy-2020/ can’t run the 40-udp-proxy-2020.sh script
Checking podman ps, only unifi os is created…
And with wireguard, I can ping my roon server, but I can’t see it anymore across roon app, however, I have configured the firewall exactly as described here: Run-a-Wireguard-VPN-server-on-UDM-Pro
Regarding boot script requirements
I am using firmware 1.10.4, can this be the reason for all these problems, what is your version?
thanks
David
I’m running UniFi OS UDM Pro 1.11.0 (latest version) so I don’t think it’s that.
When you say “can’t run the 40-udp-proxy-2020.sh script” do you meant it doesn’t run / returns an error, or just that it runs but that it then doesn’t appear as a container when running podman ps ?
If the latter I’d double check your WireGuard interface is up and running correctly.
I seem to remember hitting a similar issue and it turned out to be an issue with my Wireguard setup that was causing the udp-proxy script to run, but then fail to actually start the container, or for the container to die as soon as it was started.
Given you recently had this working, have you changed anything in your Wireguard config files? If so I’d think about what you might have changed there.
If it’s just that the script fails to run, with a ‘not found’ error like you had previously then I’m stumped, but given you recently had it working I’d think back to what might have changed.
Ah!!! I think I know what’s causing your error and it’s these instructions ….
Step 4
Create file /mnt/data/wireguard/wg0.conf
[Interface]
PrivateKey=c<your private server key here>I=
ListenPort = 51820
#Peer Number 1
[Peer]
PublicKey = O<peer number one's public key here>=
AllowedIPs = 192.168.240.2/32
This example / step doesn’t include a local interface address / IP and for some reason that causes udp-proxy to fail to start.
Add an address to that config like this and see if that helps…
[Interface]
Address: 192.168.240.1/32
PrivateKey=c<your private server key here>I=
ListenPort = 51820
@David_Ghidoni given you already have it half-setup using the older UDM Wireguard implementation I’d stick with those setup instructions and example configs for now and just add the address entry per above to the WG config file on your UDM and restart Wireguard. Otherwise you may end up causing yourself more issues / having multiple conflicting copies of Wireguard. FWIW I initially used those instructions too and hit the same issue as you, adding the address entry to my local Wireguard config fixed it.
But for others reading this is future and starting from scratch, this is what worked for me on a UDM Pro.
Step 1:
Install Wireguard per these instructions, then check you can access your Roon Core remotely. If you can’t recheck your Wireguard config.
Step 2:
In order to see your remote device (ie. a remote laptop or phone) as an audio output when connected over your Wireguard network, follow these instructions to setup udp-proxy-2020
You’ll want to use INTERFACES=br0,wg0 in your udp-proxy-2020.conf file when installing on a UDM (this differs from the USG)
Can I ask a dumb question…
If I’m trying to set up a site-to-site vpn to connect my two homes so I can try to support them with a single core in my primary home (see below thread for use case and Brian’s suggestion that I and others pursue this route) and I have UDMPro on one end and USG3 on the other…
…then why would I want to use wireguard as opposed to the “natively unifi supported” OpenVPN to create and maintain the site-to-site VPN? Is it more secure, does it offer other features? Happy to pursue this, just trying to figure out my strategy as a networking civilian with gear that ought to support my goals.
For your use case, use which ever is easier to deploy. For your hardware, that is probably OpenVPN.
That said, Wireguard is more modern, higher performance (at least on Linux systems) and secure.
Awesome. I just managed to get DDNS and OpenVPN working. I can’t yet manage to ssh into my remote Unifi USG, but I can see my RopieeeXL’s and RooExtend’s web interfaces, so I’m getting somewhere. This is an awesome learning experience - what would take you minutes takes me hours, but I feel really really psyched when I get it done. Onwards!
Ok, @Nepherte I’m really really close to getting this running on my USG (I’m trying to get this running on a UDM Pro on one end with the Docker version of udp-proxy-2020, and following these instructions for the USG on the other ends)…
I managed to copy the files and
scp -O -i ~/.ssh/207UDM_rsa.pub udp-proxy-2020-0.0.11-linux-mips64.1 admin@192.168.10.1:/home/admin/bin/udp-proxy-2020
them into the right place. I figured out the right interfaces for my OpenVPN I chmod +x’ed the file, and then tried to execute
sudo ./udp-proxy-2020 --port 9003 --interface eth1,vtun64
But the issue is that that command executed on the USG never comes back. It just sits - no response, no return to the command prompt. Any help would be most welcome! I’m not bothering to set up the script until I get the file to “run correctly”. Thanks!
Edit: FWIW, if I run without sudo, I get
FATAL eth1: Permission Denied
One further update… if I log in to a new terminal window, and try to run the same commands I get a different error:
admin@ubnt:~/bin$ sudo ./udp-proxy-2020 --port 9003 --interface eth1,vtun64
FATAL Unable to init SinkUdpPackets error="192.168.10.1:9003: listen udp4 192.168.10.1:9003: bind: address already in use
@Aaron_Turner; your detailed explanations on another thread had helped me set up a sustainable wireguard vpn for roon using an Rpi2.
With Roon ARC one would think that very few would need to look at VPNs but I am exploring a use case for this. this time, I would like to use my router directly, (ASUS RT-AX88u) which has a seamless wireguard implementation. Using this, I am able to get roon remote to see my core & connect over a mobile network but the core does not recognise the phone as a player. I guess UDPproxy would be the knight in shining armour, but am unsure how to go about it. (I assume a ARM v7 package will work – the router has a BCM49408 which is ARM v8)
If someone could guide me a bit on this, I would be very grateful.