The clue here is the reference to MultipleNatFound. This, on its own, means that either:
- Your ISP is using CG-NAT
- You have two routers in your home network.
Looking further, I can see local network ip addresses in two different subnets: 192.168.3.61 and 192.168.0.1.
This means that you definitely have two or more routers in your home network.
Note: This does not rule out the use of CG-NAT by the ISP - but, as there is nothing else that suggests CG-NAT is in play, I think that we should start of by assuming that CG-NAT is not being employed.
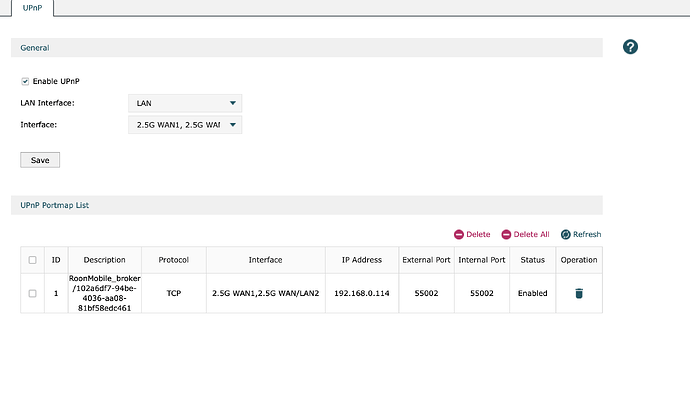
Since, the screen shot that you have posted is showing a uPnP created rule, then I am assuming that this is from the Web UI of the router to which the Roon Server is connected. Is this the primary router of a Mesh WiFi system? Do you have an ISP supplied router in addition to this router?
There are three approaches to solving this issue:
- Eliminate the multiple subnets (i.e. change the operating mode of one of the routers so that it does not perform routing [NAT]).
- Setup multiple port forwarding rules to match the multiple routers
- Use Tailscale VPN to bypass the need to set up port forwarding.
Taking these approaches one at a time:
Eliminate the multiple subnets
This can often be achieved by either:
- Setting the ISP router into ‘bridge mode’ (sometimes called ‘Modem mode’) so that all that it does is pass traffic from its WAN side to a single LAN side connection with no NAT or DHCP.
- Setting the secondary router (the one that you have posted the screen shot of the UI of) into ‘Access Point’ mode so that I only provides the Wifi connection and the additional LAN side connections. Again, this will mean that this router will not provide NAT or DHCP services.
Setup multiple port forwarding rules to match the multiple routers
This is often more complicated to setup and probably involves more configuration in your routers (plural).
I beleive that this is best done by setting up explicit port forwarding on the routers rather than relying upon uPnP so uPnP should be disabled on both routers.
To make this work reliably, the ip addresses of the devices involved should not be allowed to change. The easiest way to do this is to:
- On the ISP router, set a DHCP reservation (fixed mapping) of the secondary router WAN side IP address (192.168.3.61).
- On the Secondary router, set a DHCP reservation of the Roon Server Ip address (192.168.0.114).
Now you can setup a port forwarding rule to forward TCP traffic on the Roon ARC port (55002) on each router.
On the ISP router, the port forwarding rule should forward port 55002 TCP traffic to the WAN side address of the secondary router (192.168.3.61).
On the secondary router, the port forwarding rule should forward port 55002 TCP traffic to the ip address of the Roon Server (192.168.0.114).
Use Tailscale VPN to bypass the need to set up port forwarding
When Tailscale is used, port forwarding becomes irrelevant. The Roon ARC settings page (from which you copied the diagnostic text above) will continue to report a bad connection but Tailscale will allow ARC to access the Roon Server as if it was on the local network (and therefor does not need port forwarding).
There is a series of help centre articles on tail scale which are all linked from the overview article at:
Note, however, that with respect to RoonOS Roon Servers, the guide above only currently covers Nucleus One, Nucleus Titan and ROCK systems running RoonOS build 271 (or later) that has Tailscale built in. If you have a Nucleus, Nucleus Plus or ROCK system using BIOS boot that will not update to RoonOS Build 271, you will have to run Tailscale on an additional device (which must, like the Roon Server, be left turned on for ARC to work). In this case, the Tailscale installation must be configured to allow local network access.
Note also: The Tailscale is the only solution that you can use if your ISP is using CG-NAT other than talking to your ISP and getting them to supply a non-CG-NAT solution (usually at extra cost).