Compatibility with devices that don’t support 1.3.
Thanks, but I don’t know what Ports are it refers to service types, and I don’t know what those are either.
You said:
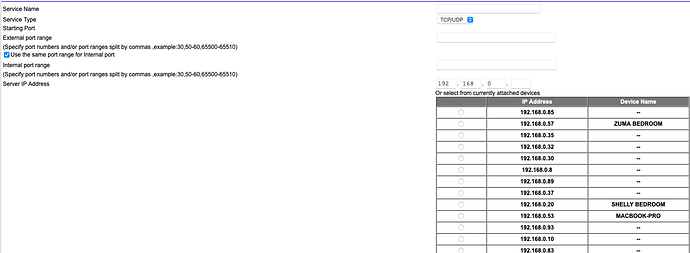
It has a fixed IP 192.168.0.5
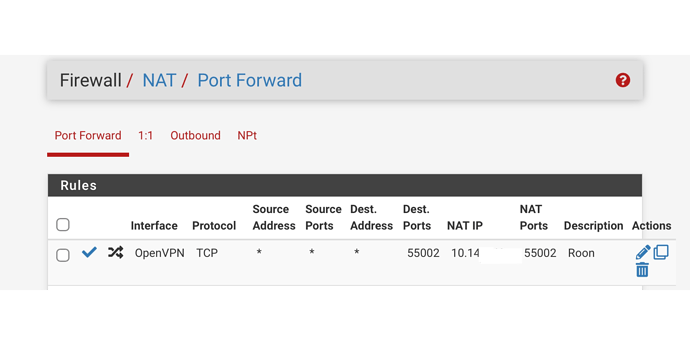
Roon created a port 55002
It then gives me this:
I don’t understand what I’m trying to do any why. All I want is to stop Roon creating a hole in my router.
Either disable uPnP on your router (this would potentially affect other software running on your network), or enter 0 as the port used under Settings > Roon ARC in Roon.
You choose to live your life in paranoia, it’s your choice. There are many relatively simple things one can do to reduce one’s attack surface, such as running separate machines with minimal authorizations for services like Roon. Many of the exploits you talk about are facilitated by “convenient” commingling of functions in a single machine where privilege escalation can then lead to exploitation of critical resources. The same way that I won’t ever mix my personal and work computing platforms, I don’t mix Roon or HQPlayer with anything of real importance on the same machine, and I the separate machines have no privileges on each other.
I did that, the QNAP rebooted and a new number appeared in the port box.
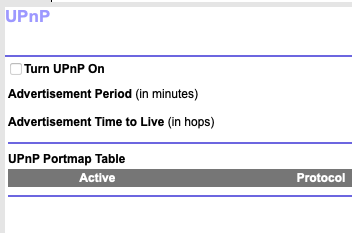
uPnP is off.
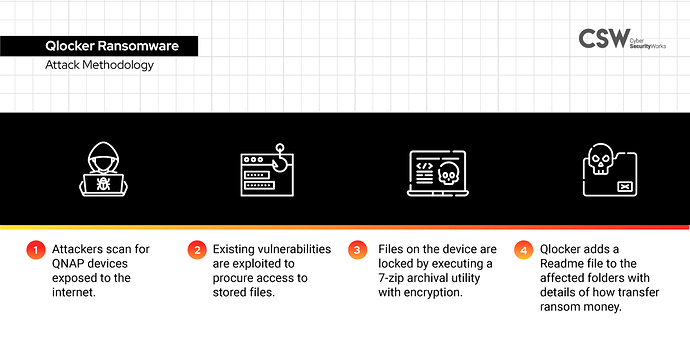
Having been a Qlocker ransomware victim, I don’t want to go through that again.
I have opened a support request for an idiot’s guide to go back to 1.8 Legacy, waiting for a reply.
I’m not sure why you want to do that?
You don’t have UPnP enabled.
You have not manually opened a port.
Therefore ARC will not work, going back to 1.8 means Roon will go out of date as you won’t get updates.
You can also set the port number to 0 in Roon to disable it as suggested above.
Thanks, most of which I don’t understand. I know ho to fix an IP address and change a password, but that’s about it.
I bought an Innuos for Roon, but now use Innuos with Sense on my main system. The TS-473 was installed for business use, it is largely empty, so I put the Roon Core on that. We use Roon throughout the house, except on the main system in the music room. It uses the music library on the Innuos.
I have network Bitdefender, Sophos, QuFirewall and a QNAP malware app running. I use 2-thingy authentication. I have disabled the admin account.
You’re missing the point. The support for all of the main versions is there. Primary choice should be use 1.3 and if not compatible then fall back to 1.2.
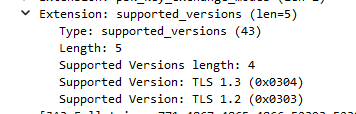
It’s the roon arc client that states the TLS version it supports and the server (core) responds with what it wants to use, in this case 1.2
Just ask your IT partner (or an IT student) to check if your router supports OpenVPN. A lot of them do.
If so, activate the VPN-server and install the client and config on your smartphones. I’ve added a screenshot of the entry I had to make on my router to make it work in my previous post.
If your router has no OpenVPN server, you can ask someone to create one for you on a PI4. A fully equipped PI4 with power supply etc. will set you back 100 USD. Software is free. That way’ you don’t have to expose your NAS to the internet.
The 473 supports QNAP virtualisation station. You can ask someone to install virtualisation station and create an OpenVPN-server inside an image in Virtualisation Station. That’s less secure than the PI road, but it is a lot more secure than exposing QTS to the internet and you will not have to buy additional hardware.
Feel free to tag me if you have questions.
Yes. You just need IPTABLES to do the port forwarding if you use a distribution to end your WireGuard tunnel.
I do exactly that in pfsense and it works.
Yet such an attack started from within your network, e.g., phishing, malvertising, malicious websites etc. not an open port in your network.
Nonetheless, there’s no need to revert to 1.8. You may use 2.0 by turning off UPnP on your router and not setting up the required port forwarding.
This may be for another thread and not related to ARC, but a valid security question. When setting up core on a ubuntu server LTS, following the documented instructions (to my recollection) core appears to run as root?
Many thanks. since that happened I got Bitdefender and it seems very good.
I think I’m going to try and find a local company to reinstall the QNAP from scratch and I can then just leave it alone. I used to need remote access, don’t need it anymore.
All the TCP, UTP, NAT terms make my head spin.
Yep. Networking is a specialty with its own lingo.
Correct.
I have complained about this for years, but the response has always been “Roon Core is running inside your firewall; it can’t be reached from the outside, so who cares whether it is running as root? If someone has already breached your firewall, you have bigger problems.”
Well, now it is reachable from the outside, so you bloody well should care.
It’s trivial to run Roon Core as a non-privileged user. I gave instructions for doing so above.
I cannot imagine turning on the ARC feature while Roon Core is still running as root.
Me, either, I’m afraid. Frankly, I don’t think Roon should be able to delete my music files, either.
Right.
That’s the main thing which “breaks” when you run Roon Core as a non-privileged user. I view preventing Roon from being able to delete my music files as a feature, not a bug.
I feel any delete action should specifically prompt for adequate permissions. rm -I has been an alias for me since I learned how to read a man page.
what would your instructions be if I were running a mac, say?