Thanks - timely as my QNAP has just prompted a firmware update.
You could always just select your own random port?
With such a small amount of users and such a random application is someone really going to go hunting for them?
On my NAS it shows zero attempted logons since it was installed.
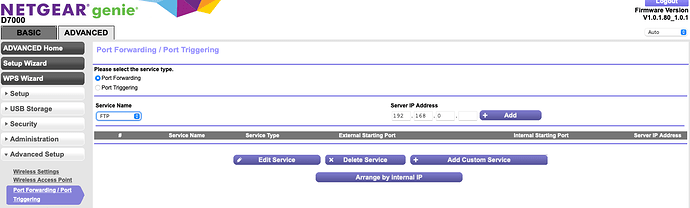
You need your core to have a fixed IP in your router, then go to the Port Forwarding page on your router and you enter the port Roon is using and assign it to the internal IP.
In my example my NAS is named so it shows the name rather than its IP.
I also gave the forwarding a name to identify it - Roon-ARC, refer to your router manual for how to forward a port.
This URL can test if the port is open - Open Port Check Tool - Test Port Forwarding on Your Router
Help from Roon below
You’re not, I’m a community member just like you. AFAIK, 1.2 isn’t depreciated, so that’s why I’m asking.
So in the interests of network security, I would be interested to know what security is actually incorporated into the Roon server software. With the multiple QNAP failures and people getting their files locked with ransomware it is something to be aware of.
Personally, all access is going to be via VPN and not just open a port manually or by upnp.
As always mileage will vary. But it is worth thinking about.
@Sean_O - Good point. I am no longer sure that running Roon on the QNAP is a good idea.
How are you telling the ARC app to find your core over VPN? Or are you bringing your VPN into the LAN network directly (rather than routed)?
I use OpenVPN that gets me on to my local network I can access everything locally. I tried ARC this morning and it just works.
There no way I’d open a port and trust Roon to be better built for security than all the other things I don’t trust. What would be great would be in Arc is workable over an existing VPN (wireguard in my case) so I’m adding no more risk to my setup. Is that doable? Wireguard in particular is designed to be simple and fast and doesn’t proxy broadcast packets so upnp discovery won’t work… is there a way to access Roon via arc in this scenario? If not, thanks for the intention but the implementation is impossible for me to trust enough to open a port for it, which is a shame.
Ok over wireguard it works fine on a remote wifi network once I’ve initially set it up on my home network – great.
I’ve so far not managed to get it to play anything on 4G mobile network here in the UK (over wireguard) – not sure if I should expect that to work or not, but it just gives me a ‘poor connection’ error regardless of how solid my data connection is.
I’m NOT going to be opening ports to try a direct connection, for security-concern reasons… but at least on wifi I can get in and listen in ‘high quality’. So that’s non zero.
So I found this page on my router. Then what? Bear in mind, as an Economist, I don’t know what a port or port forwarding is. All I know is that it lets people in.
One of the changes from 1.2 to 1.3 is that a number of obsolete and potentially dangerous protocols still in 1.2 were removed. And the security of the initial handshake was improved.
By “potentially dangerous”, I mean that well-known (to the security community) attacks have exploited those weaknesses already, and those attacks worked.
Really should use 1.3 instead of 1.2, if at all possible.
@Danny You must realise that people like me, and there are lots of us (we are the vast majority) that know nothing about networking hate having to log in to our router as we know next to nothing about them and we do not use software products that require us to get technical.
My QNAP - and I paid someone to set it up and I rarely log in to it - has an app called Qfinder Pro that lets me update the firmware (vital for security reasons, I’m told) without actually having to log in to the server directly. I did the today as there was an update and, as someone advised, the ARC port code changed.
There must be a simple switch to disable ARC and one that does not change when the Roon Core reboots.
This is a big issue - my QNAP got wiped out by ransomware in January.
The danger from security holes is not, generally speaking, from some “script kiddy” or nominal potentate from some obscure country. Or from anyone who even knows you exist or cares about what’s on your computer. It’s from large, highly automated attack systems that are looking for computers of any kind, primarily for one of three purposes:
-
To enroll in a botnet, a collection of many zombified machines that will do whatever the commander of such a net wants them to;
-
To “mine” some kind of digital currency like Bitcoin;
-
To encrypt the contents of the machine and hold the information for ransom.
These systems scan the whole Internet continuously, over and over, looking for vulnerable computers. They are inhumanly persistent and patient. Not to be too dramatic, but they don’t care who you are, what you do, or what your machine has on it; they only care about weaknesses. Anthropomorphizing this is kind of dangerous in its own right.
Sorry I misunderstood you. But why would Roon ever need to hold this kind of information? So you are saying open port for Roon Core without any proxy or segmentation? That doesn’t sound like good practice to me.
I hope limiting my machine to UK access using QuFirewall and 2-stage authentication will help. Plus three or four anti-virus and malware apps.
Yes, but those outdated cryptography features, whilst still available, shouldn’t be used, and 1.2 can be deployed securely.
I have for some time, but I’d wager that most implementations still use 1.2… it took business long enough to mobilize resources to move away from 1.0 and 1.1.
So if Roon are advertising 1.3 as an available option in the key exchange why are they using 1.2?
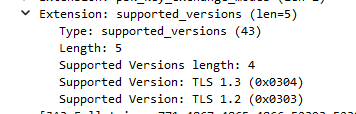
TLS v1.3 has been around for the last 4 years and Arc is a new app so why use a 14 year old vulnerable version as a preference?
If I understand correctly what you are saying, the server is advertising both TLS 1.2 and 1.3, and the iOS client is selecting 1.2.
I forget which version of iOS started supporting TLS 1.3, but it wasn’t all that long ago. If you compile the ARC app to be compatible with older versions of iOS, then it will default to TLS 1.2, 'cuz that’s what those versions of iOS supported.
The screen shots look the same , I would try and follow the instructions below.