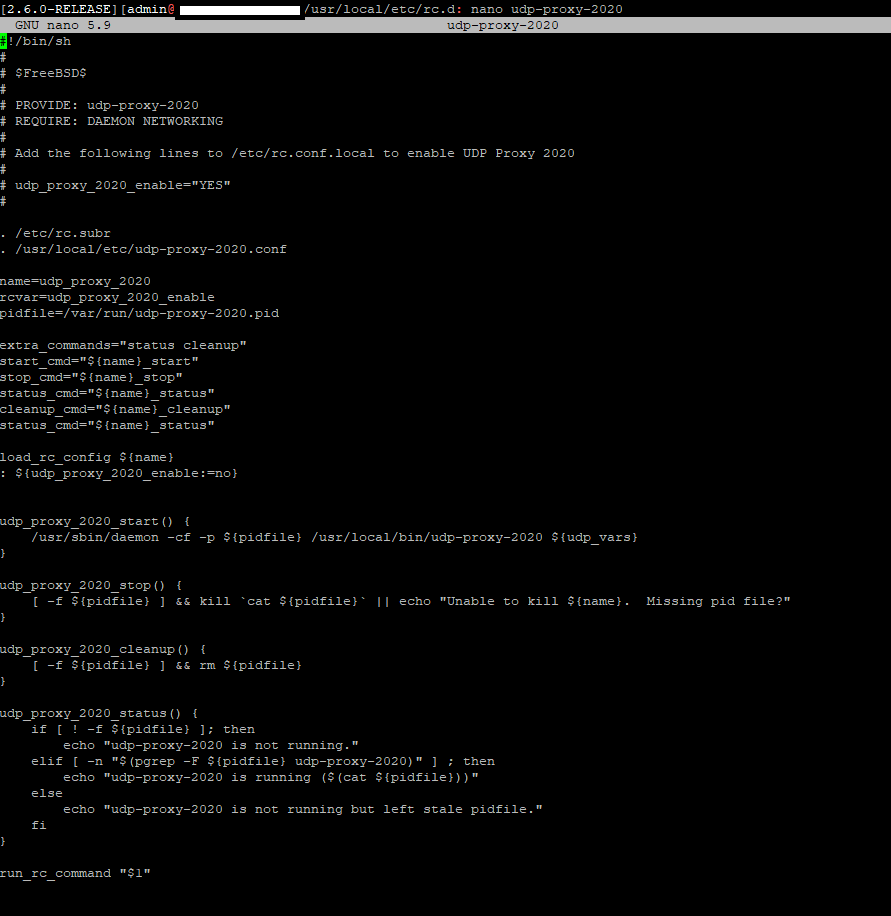
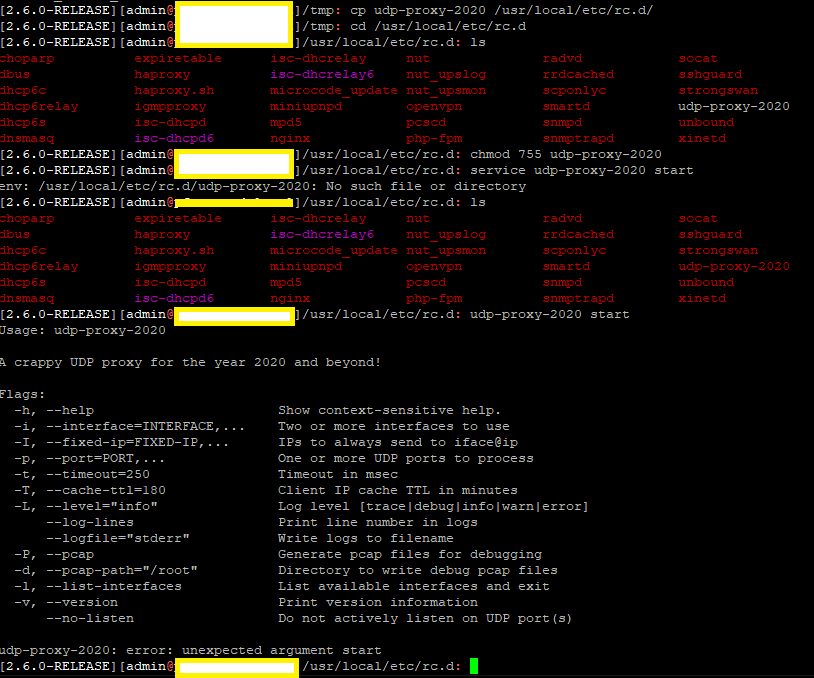
I hope I’m not necroing a thread. But I thought it would be helpful to have this config under the same topic. I have a slightly different configuration at home with my multi VLAN network. I’m using a /20 at home and the RoonCore (docker container) is running on 10.0.10.110. I have the 10.0.0.0/24 (wired) and 10.0.2.0/24 (wireless). I’m not using pfSense as the Layer 3 device between VLANs. I’m using a Cisco switch (3750) for that. At first, I setup mDNS rebroadcasting on the switch to re-broadcast mDNS traffic between certain VLANs. I went with a “nuke it from orbit” config on the switch for that:
service-list mdns-sd PERMIT-ALL permit 10
service-routing mdns-sd
interface Vlan10
description Home LAN
ip address 10.0.0.1 255.255.255.0
ip pim sparse-dense-mode
service-routing mdns-sd
service-policy PERMIT-ALL IN
service-policy PERMIT-ALL OUT
redistribute mdns-sd
interface Vlan12
description Home WLAN
ip address 10.0.2.1 255.255.255.0
ip helper-address 10.0.10.255
ip pim sparse-dense-mode
service-routing mdns-sd
service-policy PERMIT-ALL IN
service-policy PERMIT-ALL OUT
redistribute mdns-sd
interface Vlan19
description Home Media
ip address 10.0.9.1 255.255.255.0
ip pim sparse-dense-mode
service-routing mdns-sd
service-policy PERMIT-ALL IN
service-policy PERMIT-ALL OUT
redistribute mdns-sd
interface Vlan20
description Home Server
ip address 10.0.10.1 255.255.255.0
ip pim sparse-dense-mode
service-routing mdns-sd
service-policy PERMIT-ALL IN
service-policy PERMIT-ALL OUT
redistribute mdns-sd
Unfortunately, Roon doesn’t use blanket multicast for all devices (for some unknown, horrible reason). It does seem to utilize multicast for Chromecast devices (and maybe AirPlay?) So, to get this working (along with a Linux laptop running Roon Bridge, which is also running firewalld), I needed to find out the ports that Roon uses, which seems to have changed over the different versions. If there’s a single place that has all the port requirements, I haven’t found it. It is absolutely essential that this info is published. For my Roon 2.0 (CORE Build 1193, Linux Bridge 1.8 Build 125, Android 2.0 Build 1192) it appears that Roon (of various types above) send to the subnet’s broadcast address on the destination port 9003. On the Cisco switch, I had to enable a combo of ip helper-address, ip forward-protocol (with an accompanying extended ACL) and ip directed-broadcast (with that same ACL). Below is the complete config combining the above and the new commands:
service-list mdns-sd PERMIT-ALL permit 10
service-routing mdns-sd
ip forward-protocol udp 9003
#Roon Server IP is 10.0.10.110)
access-list 100 permit udp host 10.0.10.110 any eq 9003
interface Vlan10
description Home LAN
ip address 10.0.0.1 255.255.255.0
ip helper-address 10.0.10.255
ip directed-broadcast 101
ip pim sparse-dense-mode
service-routing mdns-sd
service-policy PERMIT-ALL IN
service-policy PERMIT-ALL OUT
redistribute mdns-sd
interface Vlan12
description Home WLAN
ip address 10.0.2.1 255.255.255.0
ip helper-address 10.0.10.255
ip directed-broadcast 101
ip pim sparse-dense-mode
service-routing mdns-sd
service-policy PERMIT-ALL IN
service-policy PERMIT-ALL OUT
redistribute mdns-sd
interface Vlan20
description Home Server
ip address 10.0.10.1 255.255.255.0
ip helper-address 10.0.0.255
ip helper-address 10.0.2.255
ip directed-broadcast 101
ip pim sparse-dense-mode
service-routing mdns-sd
service-policy PERMIT-ALL IN
service-policy PERMIT-ALL OUT
redistribute mdns-sd
The above config is saying we’ll allow broadcasts on UDP 9003 (forward command). We then create an ACL for allowing the Roon Server to talk to anything on 9003/UDP We then apply that directed broadcast command on each VLAN interface and telling it to use the ACL 100 we created above. Next, we have to tell each interface where it’s allowed to send it’s broadcasts (the destination of the broadcasts). On the SERVER VLAN (where Roon lives) we tell it that it can broadcast into the WIRED and WIRELESS VLANs. Since the ROON BRIDGE and other ROON CAPABLE devices can also broadcast, we go the WIRED and WIRELESS VLANs and tell them that they can broadcast back into the SERVER VLAN. This is accomplished with the IP HELPER-ADDRESS command pointing to the BROADCAST address of the /24 network (10.0.0.255 or 10.0.2.255 or 10.0.10.255).
After doing all this, I now no longer have to put in the Roon Core IP address in all my computer end points. It just shows up automagically. However, there were still some issues WRT firewalld and opening ports. Long story short, here are the ports I had to open just for other Roon devices (my Android phone for example) to even see the Roon Bridge I installed on my Arch laptop:
sudo firewall-cmd --permanent --new-service=RoonBridge
sudo firewall-cmd --permanent --service=RoonBridge --set-description=Inbound from RoonServer
sudo firewall-cmd --permanent --service=RoonBridge --set-short=SVC_IN_RoonBridge
sudo firewall-cmd --permanent --service=RoonBridge --add-port=9100-9200/tcp
sudo firewall-cmd --permanent --service=RoonBridge --add-port=9330-9332/tcp
sudo firewall-cmd --permanent --service=RoonBridge --add-port=9003/udp
sudo firewall-cmd --permanent --service=RoonBridge --add-port=1900/udp
sudo firewall-cmd --permanent --service=RoonBridge --add-protocol=igmp
sudo firewall-cmd --permanent --zone=home --add-rich-rule=' rule family="ipv4" source address="10.0.10.110/32" port protocol="tcp" accept'
sudo firewall-cmd --permanent --zone=home --add-service=RoonBridge
sudo firewall-cmd --reload
Even after these commands were added, and the Roon Bridge was now visible, I still couldn’t enable my DAC. Using the app on my phone to enable the DAC, the field was stuck on “Enabling” and not letting me enter a name for the DAC. After setting firewalld to log all denies and searching the journalctl for anything from the IP of my Android phone, I found that Roon on the phone (and presumably other devices) will use a random high numbered port to name the DAC. Once I enabled that port, the naming field immediately became available and writeable. I will be honest that I didn’t look through a pcap on my laptop for that port number listed in the INFO of a packet coming in on a broadcast or another packet. My point here is, how does Roon Remote (Android) tell the Bridge what port to listen on for the device rename? Why is this not an API on one of the already known ports? Or why doesn’t RoonBridge “open” this port on the firewall (using info gathered from other established states) by implementing a source IP and port / dest IP and port reversal so the state is already open on the local firewall?
Don’t get my started on the whole “Roon uses UDP to send audio traffic” thing.
“I’d tell you a UDP joke, but you probably wouldn’t get it.”
If there’s anything I missed or got wrong, please let me know. Thank you!!
![]()