Hi all,
Since this thread is one of the top hits on google for trying to get this to work… I figured id post what i did to get it working on pfSense.
I have my Roon Core on my vlan12 and my workstation on vlan11.
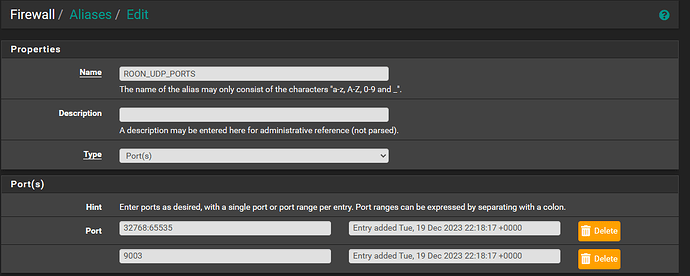
First i created a port alias with all the Roon UDP ports:
UDP 32768:65535, 9003
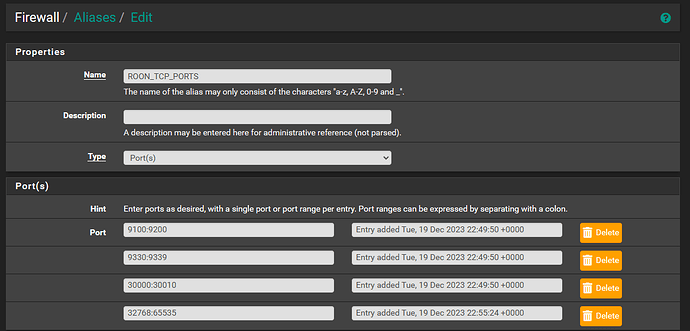
Then i created a port alias with all the Roon TCP ports:
TCP 9100:9200, 9330:9339, 30000:30010, 32768:65535
Then created an IP Alias with the IP of my Roon Core and another IP Alias for the IP of my Workstation.
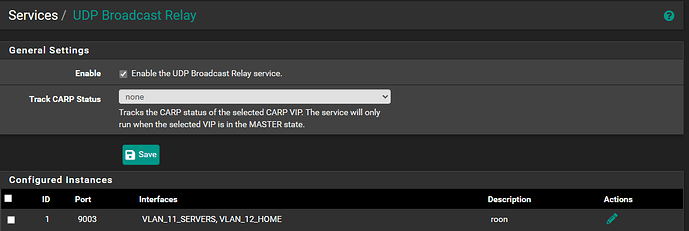
After those were completed, I installed the UDP Broadcast Relay from the Package Manager. And added a configured instance of:
ID: 1
Port: 9003
Interfaces: vlan11 and vlan12
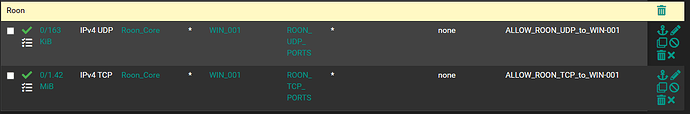
I then created two firewall rules on each vlan interface (vlan 11 and vlan 12):
VLAN_12:
IPv4 UDP Only
Source: Roon_Core (roon core alias)
Destination: WIN_001 (workation alias)
Destination Ports: ROON_UDP_PORTS (Port alias created previously with all UDP ports required)
IPv4 TCP Only
Source: Roon_Core (roon core alias)
Destination: WIN_001 (workstation alias)
Destination Ports: ROON_TCP_PORTS (Port alias created previously with all TCP ports required)
In terms of the other way around from my Workstation to Roon Core, i needed to add the entire subnet to the rules, as it sends packets to the broadcast/gateway IP addresses of both the vlan11 and vlan12.
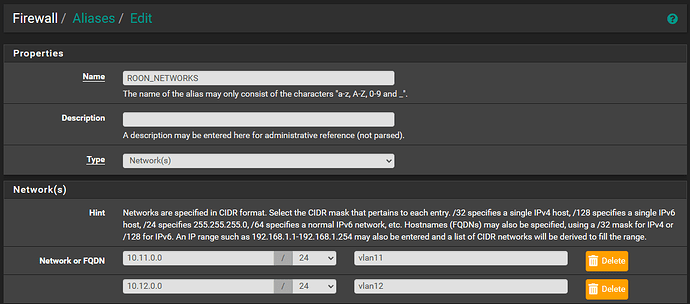
I created an IP-Network Alias with both my vlan11 and vlan12 subnets in them:
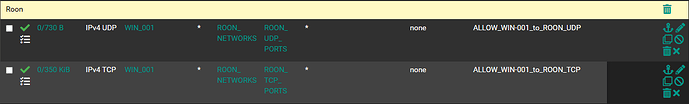
I then created 2 firewall rules on the VLAN11 interface:
VLAN_11:
IPv4 UDP Only
Source: WIN_001 (alias for my workstation)
Destination: ROON_NETWORKS (alias created previously with both subnets)
Destination ports: ROON_UDP_PORTS (alias created previously with all required UDP ports)
IPv4 TCP Only
Source: WIN_001 (alias for my workstation)
Destination: ROON_NETWORKS (alias created previously with both subnets)
Destination ports: ROON_TCP_PORTS (alias created previously with all required TCP ports)
Once that was all done, i was able to launch Roon on my Windows Workstation and control and stream music successfully. Both streaming from my iFi Zen DAC attached directly to my Roon Core, as well as using my speakers connected to my Windows workstation.
I was running around in circles trying to get it to work previously, so hopefully this helps someone else!