Hi Peter,
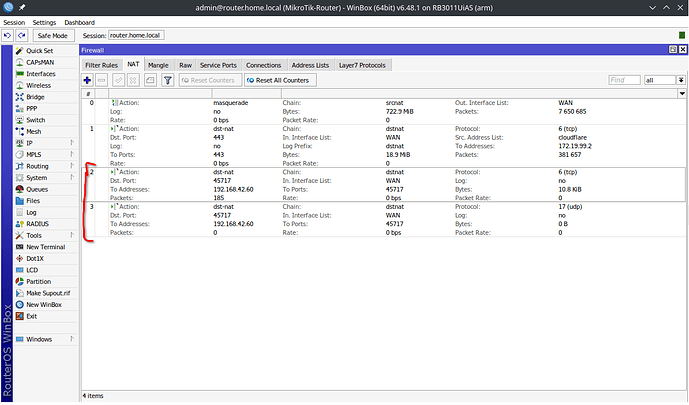
See below for the router config dumb, I truncated most of the DHCP server leases, just to reduce clutter a bit (but left in the static lease for Roon)
# nov/04/2022 05:15:44 by RouterOS 6.48.1
# software id = 3HYE-AGAS
#
# model = RouterBOARD 3011UiAS
# serial number = 8EEB08825DE4
/interface ethernet
set [ find default-name=ether1 ] speed=100Mbps
set [ find default-name=ether2 ] speed=100Mbps
set [ find default-name=ether3 ] speed=100Mbps
set [ find default-name=ether4 ] speed=100Mbps
set [ find default-name=ether5 ] speed=100Mbps
set [ find default-name=ether6 ] speed=100Mbps
set [ find default-name=ether7 ] speed=100Mbps
set [ find default-name=ether8 ] speed=100Mbps
set [ find default-name=ether9 ] speed=100Mbps
set [ find default-name=ether10 ] speed=100Mbps
set [ find default-name=sfp1 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full
/interface bonding
add mode=802.3ad name=bonding1 slaves=ether1,ether2 transmit-hash-policy=\
layer-2-and-3
/interface vlan
add interface=bonding1 name=vlan-dmz vlan-id=999
add interface=bonding1 name=vlan-iot-nointernet vlan-id=20
add interface=bonding1 name=vlan-iot-nolan vlan-id=21
add interface=bonding1 name=vlan-lan vlan-id=42
add interface=bonding1 name=vlan-mgmt vlan-id=666
/interface list
add name=LAN
add name=WAN
add exclude=dynamic name=discover
add name=mactel
add name=mac-winbox
add name=MGMT
add comment="includes LAN and MGMT" include=LAN,MGMT name=InternetOK
add name=IOT
add name=list1
add comment="Includes LAN and MGMT lists" include=LAN,MGMT name=LocalDNS
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip ipsec profile
add dh-group=modp1024 enc-algorithm=aes-256,aes-128,3des name=profile_1
/ip ipsec peer
add local-address=192.168.42.2 name=peer2 passive=yes profile=profile_1
/ip pool
add name=dhcp42 ranges=192.168.42.100-192.168.42.254
add name=dhcp666 ranges=172.16.66.100-172.16.66.254
add name=dhcp999 ranges=172.19.99.100-172.19.99.254
add name=dhcp20 ranges=10.20.20.10-10.20.20.254
add name=dhcp21 ranges=10.21.21.10-10.21.21.254
/ip dhcp-server
add address-pool=dhcp42 disabled=no interface=vlan-lan lease-time=1d name=\
dhcp-lan
add address-pool=dhcp666 disabled=no interface=vlan-mgmt lease-time=1d name=\
dhcp-mgmt
add address-pool=dhcp999 disabled=no interface=vlan-dmz lease-time=1d name=\
dhcp-dmz
add address-pool=dhcp20 disabled=no interface=vlan-iot-nointernet lease-time=\
1d name=dhcp-iotnowan
add address-pool=dhcp21 disabled=no interface=vlan-iot-nolan lease-time=1d \
name=dhcp-iotnolan
/interface ovpn-client
add certificate=client-cert-***** cipher=aes256 connect-to=\
ovpn.*****.*** mac-address=02:8E:83:31:B0:82 name=ovpn-out1 \
port=443 profile=default-encryption use-peer-dns=no user=**** \
verify-server-certificate=yes
/routing ospf instance
set [ find default=yes ] router-id=192.168.42.1
/snmp community
set [ find default=yes ] addresses=0.0.0.0/0
add addresses=::/0 authentication-protocol=SHA1 encryption-protocol=AES name=\
MtikSnmp
/user group
set full policy="local,telnet,ssh,ftp,reboot,read,write,policy,test,winbox,pas\
sword,web,sniff,sensitive,api,romon,dude,tikapp"
/ip neighbor discovery-settings
set discover-interface-list=all
/interface l2tp-server server
set enabled=yes use-ipsec=required
/interface list member
add interface=ether10 list=WAN
add interface=vlan-lan list=LAN
add interface=vlan-mgmt list=MGMT
add interface=vlan-dmz list=InternetOK
add interface=vlan-iot-nolan list=InternetOK
add interface=vlan-iot-nointernet list=IOT
add interface=vlan-iot-nolan list=IOT
add interface=ether9 list=MGMT
add interface=ovpn-out1 list=LocalDNS
/interface ovpn-server server
set auth=sha1 cipher=aes256 netmask=32
/ip address
add address=192.168.42.1/24 interface=vlan-lan network=192.168.42.0
add address=172.16.66.1/24 interface=vlan-mgmt network=172.16.66.0
add address=172.19.99.1/24 interface=vlan-dmz network=172.19.99.0
add address=10.21.21.1/24 interface=vlan-iot-nolan network=10.21.21.0
add address=10.20.20.1/24 interface=vlan-iot-nointernet network=10.20.20.0
add address=192.168.13.37/24 comment="Emergency/accident management. No DHCP" \
interface=ether9 network=192.168.13.0
/ip dhcp-client
add disabled=no interface=ether10 use-peer-dns=no
/ip dhcp-server lease
<-- truncated -->
# static reservation for roon
add address=192.168.42.60 client-id=\
ff:19:ed:27:ce:0:2:0:0:ab:11:86:a1:e1:3f:75:70:50:b9 mac-address=\
DA:9D:B6:33:7C:9D server=dhcp-lan
/ip firewall address-list
add address=173.245.48.0/20 list=cloudflare
add address=103.21.244.0/22 list=cloudflare
add address=103.22.200.0/22 list=cloudflare
add address=103.31.4.0/22 list=cloudflare
add address=141.101.64.0/18 list=cloudflare
add address=108.162.192.0/18 list=cloudflare
add address=190.93.240.0/20 list=cloudflare
add address=188.114.96.0/20 list=cloudflare
add address=197.234.240.0/22 list=cloudflare
add address=198.41.128.0/17 list=cloudflare
add address=162.158.0.0/15 list=cloudflare
add address=172.64.0.0/13 list=cloudflare
add address=131.0.72.0/22 list=cloudflare
add address=172.16.66.25 list=upsmon
add address=172.16.66.40 list=upsmon
add address=172.16.66.41 list=upsmon
add address=192.168.42.80 list=kodi
add address=192.168.42.81 list=kodi
add address=1.1.1.1 list=knowndns
add address=1.0.0.1 list=knowndns
add address=8.8.8.8 list=knowndns
add address=8.8.4.4 list=knowndns
add address=104.16.0.0/13 list=cloudflare
add address=104.24.0.0/14 list=cloudflare
add address=10.21.21.2 list=homeassistant
add address=10.21.21.5 list=miners
add address=10.21.21.11 list=roomba
/ip firewall filter
add action=fasttrack-connection chain=forward comment=\
"fasttrack and accept established/related forwarding traffic" \
connection-state=established,related
add action=drop chain=input comment="drop port scanners" src-address-list=\
"port scanners"
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=1w chain=input comment="add any connection attempts t\
o FTP, telnet, SSH on WAN to port scanner list" dst-port=20-23 \
in-interface-list=WAN protocol=tcp
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment=\
"add detected port scanners to list" in-interface-list=WAN psd=21,3s,3,1 \
src-address-list=!knowndns
add action=accept chain=input comment=\
"accept established, related, untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="drop invalid connections on input chain" \
connection-state=invalid
add action=accept chain=input comment="accept icmp on non-WAN interfaces" \
in-interface-list=!WAN protocol=icmp
add action=accept chain=input comment=\
"accept DNS (TCP/53) from Local DNS allowed interfaces" dst-port=53 \
in-interface-list=LocalDNS protocol=tcp
add action=accept chain=input comment=\
"accept DNS (UDP/53) from Local DNS allowed interfaces" dst-port=53 \
in-interface-list=LocalDNS protocol=udp
add action=accept chain=input comment="accept from management group" \
in-interface-list=MGMT
add action=drop chain=input comment="drop everything else on input chain" \
log-prefix="input drop"
add action=passthrough chain=forward in-interface=ovpn-out1 log=yes
add action=passthrough chain=forward log=yes out-interface=ovpn-out1
add action=drop chain=forward comment="drop port scanners" src-address-list=\
"port scanners"
add action=drop chain=forward comment=\
"drop invalid connections on forward chain" connection-state=invalid \
log-prefix="drop invalid"
add action=drop chain=forward comment="Drop roomba connections to WAN" \
out-interface-list=WAN src-address-list=roomba
add action=accept chain=forward comment="accept established, related" \
connection-state=established,related
add action=accept chain=forward comment=\
"accept InternetOK traffic going to WAN" in-interface-list=InternetOK \
out-interface-list=WAN
add action=accept chain=forward comment=\
"accept NFS (TCP/2049) connections from dmz servers to NAS" dst-address=\
192.168.42.25 dst-port=2049 in-interface=vlan-dmz protocol=tcp
add action=accept chain=forward comment="accept cctv traffic to nowan vlan" \
out-interface=vlan-iot-nointernet src-address=172.19.99.3
add action=accept chain=forward comment=\
"accept http(s) (TCP/80, TCP/443) connections from LAN to DMZ proxy" \
dst-address=172.19.99.2 dst-port=80,443 in-interface-list=LAN protocol=\
tcp
add action=accept chain=forward comment=\
"allow direct ip emby access from LAN (for the app, TCP/8096)" \
dst-address=172.19.99.4 dst-port=8096 in-interface-list=LAN protocol=tcp
add action=accept chain=forward comment=\
"accept docker management (TCP/2375) connections to dmz" dst-port=2375 \
out-interface=vlan-dmz protocol=tcp src-address=192.168.42.26
add action=accept chain=forward comment=\
"accept HTTP (TCP/80) from LAN to IOT proxy" dst-address=10.21.21.3 \
dst-port=80 in-interface-list=LAN protocol=tcp
add action=accept chain=forward comment=\
"accept HTTP (TCP/80) from inbound VPN to IOT proxy" dst-address=\
10.21.21.3 dst-port=80 in-interface=ovpn-out1 protocol=tcp
add action=accept chain=forward comment=\
"Accept HTTP (TCP/80) traffic from MGMT to IOT proxy" dst-address=\
10.21.21.3 dst-port=80 in-interface-list=MGMT protocol=tcp
add action=accept chain=forward comment="accept NUT UPS Monitor connections (T\
CP/3493) from HomeAssistant to NUT servers" dst-address-list=upsmon \
dst-port=3493 protocol=tcp src-address-list=homeassistant
add action=accept chain=forward comment=\
"accept Logitech Media Server connections (TCP/9000) from HomeAssistant" \
dst-address=192.168.42.26 dst-port=9000 protocol=tcp src-address-list=\
homeassistant
add action=accept chain=forward comment=\
"accept Kodi control connections (TCP/8080) from HomeAssistant" \
dst-address-list=kodi dst-port=8080 protocol=tcp src-address-list=\
homeassistant
add action=accept chain=forward comment="Allow MGMT traffic to miners" \
dst-address-list=miners in-interface-list=MGMT
add action=accept chain=forward comment="accept MGMT traffic to ovpn network" \
in-interface-list=MGMT out-interface=ovpn-out1
add action=accept chain=forward comment="accept ovpn traffic to MGMT" \
in-interface=ovpn-out1 out-interface-list=MGMT
add action=accept chain=forward comment="accept LAN traffic to ovpn network" \
in-interface-list=LAN out-interface=ovpn-out1
add action=accept chain=forward comment="accept ovpn traffic to LAN" \
in-interface=ovpn-out1 out-interface-list=LAN
add action=accept chain=forward comment="accept from WAN if DSTNATed" \
connection-nat-state=dstnat in-interface-list=WAN log-prefix="accept wan"
add action=drop chain=forward comment="drop and log everything else from WAN" \
in-interface-list=WAN log=yes log-prefix="drop wan"
add action=drop chain=forward comment="isolate vlans" in-interface=vlan-dmz \
log-prefix=dmzdrop out-interface=!vlan-dmz
add action=drop chain=forward comment="isolate vlans" in-interface=!vlan-dmz \
log-prefix=a out-interface=vlan-dmz
add action=drop chain=forward comment="isolate vlans" in-interface=\
vlan-iot-nointernet out-interface=!vlan-iot-nointernet
add action=drop chain=forward comment="isolate vlans" in-interface=\
!vlan-iot-nointernet out-interface=vlan-iot-nointernet
add action=drop chain=forward comment="isolate vlans" in-interface=\
vlan-iot-nolan out-interface=!vlan-iot-nolan
add action=drop chain=forward comment="isolate vlans" in-interface=\
!vlan-iot-nolan out-interface=vlan-iot-nolan
add action=drop chain=forward comment="isolate vlans" in-interface=vlan-lan \
out-interface=!vlan-lan
add action=drop chain=forward comment="isolate vlans" in-interface=!vlan-lan \
out-interface=vlan-lan
add action=drop chain=forward comment="isolate vlans" in-interface=vlan-mgmt \
out-interface=!vlan-mgmt
add action=drop chain=forward comment="isolate vlans" in-interface=!vlan-mgmt \
out-interface=vlan-mgmt
add action=drop chain=forward comment="drop everything else on forward chain" \
log-prefix="drop forward"
/ip firewall nat
add action=masquerade chain=srcnat out-interface-list=WAN
add action=dst-nat chain=dstnat dst-port=443 in-interface-list=WAN \
log-prefix=dstnat protocol=tcp src-address-list=cloudflare to-addresses=\
172.19.99.2 to-ports=443
add action=dst-nat chain=dstnat dst-port=45717 in-interface-list=WAN \
protocol=tcp to-addresses=192.168.42.60 to-ports=45717
add action=dst-nat chain=dstnat dst-port=45717 in-interface-list=WAN \
protocol=udp to-addresses=192.168.42.60 to-ports=45717
/ip ipsec identity
add peer=peer2
/ip route
add distance=1 dst-address=192.168.1.0/24 gateway=ether10
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh address=172.16.66.0/24 disabled=yes
set www-ssl address=172.16.66.0/24,192.168.13.0/24 certificate=BagEndRos \
disabled=no
set api disabled=yes
set winbox address=172.16.66.0/24,192.168.13.0/24
set api-ssl address=172.16.66.0/24 certificate=BagEndRos
/lcd interface pages
set 0 interfaces=\
ether1,ether2,ether3,ether4,ether5,sfp1,ether6,ether7,ether8,ether9,*B
/routing ospf network
add area=backbone network=192.168.255.0/24
add area=backbone network=192.168.42.0/24
/snmp
set enabled=yes trap-community=MtikSnmp
/system clock
set time-zone-name=America/Los_Angeles
/system identity
set name=MikroTik-Router
/system logging
add disabled=yes topics=ospf
/tool mac-server
set allowed-interface-list=mactel
/tool mac-server mac-winbox
set allowed-interface-list=mac-winbox
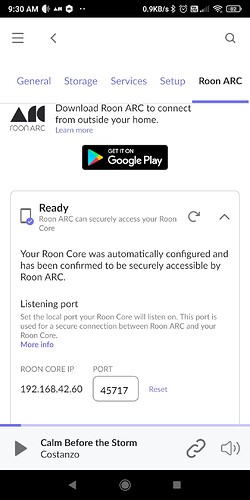
I’ll note that my issue seems a bit different from the issue in the thread you linked; Roon itself is reporting that ARC is set up correctly, and when I use the button to refresh/test again, I can see the packet counters on the dst-nat rule to forward the Roon port increment.
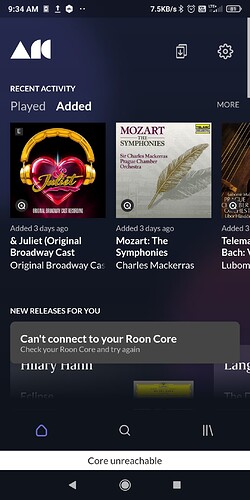
The Roon ARC app seems to be unable to connect remotely (fwiw the same phone while on the same mobile connection is able to connect to some other services that are also hosted at home with port forwarding, like my security cameras).